Card Recon is a trusted and specialized Cardholder Data Discovery tool, widely used in the PCI QSA community. It helps organizations comply with PCI DSS by accurately and efficiently locating sensitive cardholder data (CHD).
Both editions include command-line support; GUI available on Windows.
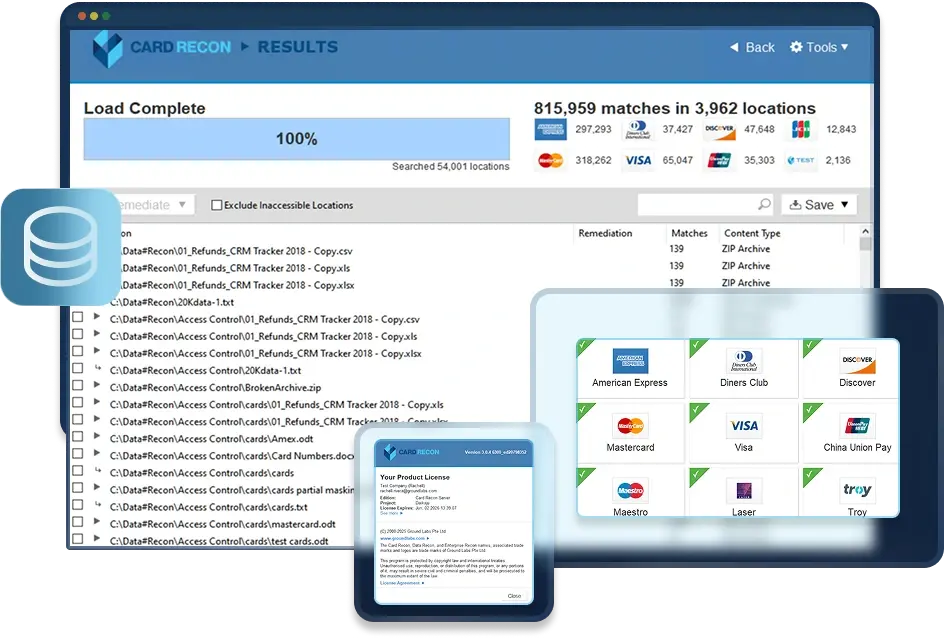
Card Recon by Ground Labs is the award-winning PCI DSS scoping and remediation solution trusted by QSAs.
pre-configured credit
card data patterns
major card brands and
private-label cards
PCI QSAs trust
Ground Labs

Card Recon delivers targeted data discovery for simplified PCI DSS scoping, preconfigured with account number formats from all payment card major providers.

Packaged with instant remediation options for rogue account data, Card Recon enables rapid response, ensuring continuous PCI DSS compliance.

Delivered with QSA-ready reporting as standard, Card Recon also provides targeted scope validation and data discovery for QSAs and PFIs, streamlining assessments and data breach investigations.

Card Recon offers fast, accurate discovery and remediation with minimal impact on performance, running without installation on most on-prem systems.








Purpose-built payment card data discovery and remediation for PCI DSS compliance.


Identification and remediation for all major card brands worldwide and private-label cards.

Extensive discovery algorithms that deliver fast, accurate search results, with powerful detection and validation filters to minimize false positives.

Instant remediation built in to manage unauthorized data stores, including masking, secure deletion, quarantine and encryption.

Deep scanning for structured and unstructured stores of data across local storage and local memory of supported desktops and servers.
Full-file scanning for all file types including OCR and archived storage, enabling discovery in scanned documents, images and compressed files.
Discovery of payments information within audio files and call recordings, enabled by advanced audio recognition technology.

Offers comprehensive and easy-to-read compliance reports in a range of exportable formats.

Designed to run independently, with no installation required, Card Recon is lightweight with no impact on system performance.
Card Recon enables rapid discovery and remediation of cardholder data across user and endpoint devices.
Lightweight PCI DSS data discovery and remediation for end-user devices.

Pre-defined patterns for all major pre-paid, debit, credit cards worldwide

Windows and MacOS desktop support

Local storage, free space, shadow volume and volatile memory scanning

Assessment-ready reporting

Out-of-the-box payment card data discovery and remediation for servers and end-user devices.
All features of Card Recon Desktop, and

Support for server-based discovery, including Windows, Linux, Solaris, HP and more

Audio file recognition, OCR and image scanning
Verifone is committed to protecting customer payment data. We began with Card Recon to achieve PCI compliance, then expanded to Enterprise Recon PII to scan back-end servers and databases. Now, Enterprise Recon PII is integral to how we manage sensitive data — providing centralized visibility, continuous compliance, and greater awareness of where data is stored, all while maintaining customer trust.
Manager, Cloud Services Systems
Corporations have data stored in so many locations that it is impossible to manually look for information. With the data security tool from Ground Labs, it makes the process easy and simple for organizations to search for data that is stored in a non-secure manner and take corrective actions to remediate it and secure the data.
CEO
In this time and age, we need to double-check some products findings, Enterprise Recon is one of the products I trust and use to double-check other products’ findings.
Information Systems Security Officer
Organizations today need to be aware of what data they handle, where they store it and what controls they have to protect it. Ground Labs develops products that fit this requirement. The tools are easy to use yet provide incredibly valuable information that can be acted on for further analysis or remedial efforts. The applications support most popular operating systems, databases and also a number of online applications.
COO
Card Recon is very effective at finding credit card numbers. Unlike many of the freeware products, Card Recon will report credit card numbers stored in a number of different formats including Excel spreadsheets, documents, emails, zip files, even recursive zip files.
Chief Security Officer QSA CISA CISSP CISM

Talk to one of our experts to discover how Ground Labs can help you take control of your data.