Organizations today manage increasingly fragmented environments, distributed across on-premises, third-party hosted and cloud-based environments and services. These diverse networks mean organizations can no longer depend on a hardened perimeter to protect them from cyber-attack. Zero-trust architectures provide an alternative approach to cybersecurity by focusing on identifying and protecting critical resources — data, applications, assets and services (DAAS) — through situationally dynamic authentication and verification controls.
Zero Trust is a cybersecurity strategy that operates on the principle of "never trust, always verify." It assumes that threats can exist both inside and outside traditional network boundaries. Therefore, it requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are within or outside of the network perimeter. This approach minimizes the chances of unauthorized access and makes security more flexible and adaptive to changes in the environment.
Data is the heart of zero trust, since, without a clear understanding of its data, organizations cannot identify these critical resources.
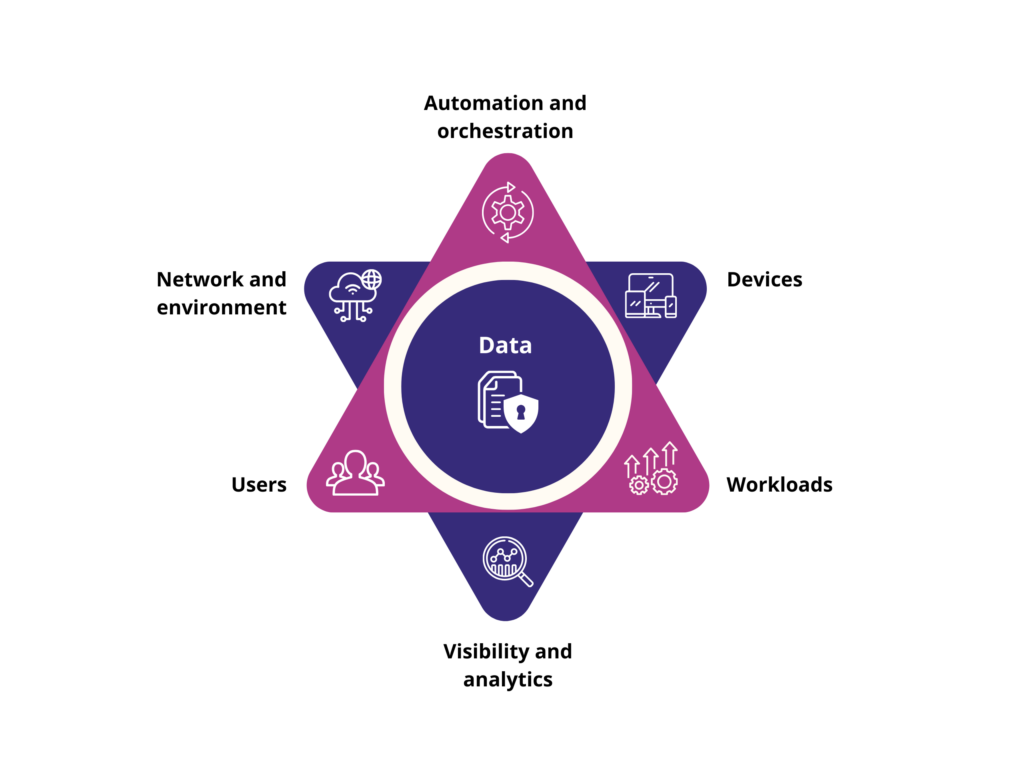
Organizations looking to implement zero trust must start by identifying their data, then evaluating and classifying it based on its sensitivity and criticality. From there, they can identify the supporting resources that store, process and transmit critical and sensitive data assets.
This process defines the scope of the zero-trust architecture and identifies the resources to which authentication and verification mechanisms will be applied, controlling and monitoring who has access to what, when and how.
As organizations develop maturity in their zero-trust environments, they’ll need to continuously identify and classify data assets within a resource inventory using automated discovery and tracking. CISA’s Zero Trust Maturity Model explains that this inventory needs to include all structured and unstructured files and data fragments across all system types and locations, as well as its associated metadata.
Organizations that successfully deliver zero trust are those that invest in accurate, evidence-based discovery to identify and classify their data assets, and do so repeatedly to inform and maintain their resource inventory effectively.
Learn more about evidence-based discovery in our complimentary e-guide, A Tech Guide to Data Discovery.

