According to Gartner, Data Security Posture Management (DSPM) “provides visibility as to where sensitive data is, who has access to that data, how it has been used, and what the security posture of the data stored or application is.” It is a practice that enables businesses maintain the confidentiality, integrity and availability of sensitive data.
In its Hype Cycle for Data Security, 2022, Gartner identified DSPM as a transformational benefit to enterprises. Organizations today manage data within complex and distributed environments, processing vast volumes of sensitive data and business critical information. DSPM offers visibility of sensitive data, enabling them to implement controls and monitor performance for effective data security.
To implement DSPM, organizations need to create an inventory of sensitive and critical information and establish who has access to those assets. Since at least 80% of data is stored in unstructured formats, most businesses can’t rely on data flow diagrams alone.
Data flows help map the expected path of data through an organization’s systems and processes. Data flows are typically developed based on formal business processes — the way things are designed to work. They tend to fall short, however, when it comes to understanding where the data truly resides — the way things actually work.
Implementing a more evidence-based approach to understanding the data they have, where it is and who can access it is crucial for effective DSPM. This can be achieved using data discovery solutions that scan for sensitive data in structured and unstructured forms, and across on-premises and cloud systems, such as Ground Labs’ Enterprise Recon.
As well as initial data discovery, Enterprise Recon includes a range of in-built remediation and data management features. Enterprise Recon Pro offers data access management. This feature provides visibility of access permissions to identified data assets and the ability to modify them as needed.
Utilizing solutions such as Enterprise Recon enables the automation of discovery and data risk management. Continuous monitoring of the data environment through frequent scanning further supports effective DSPM.
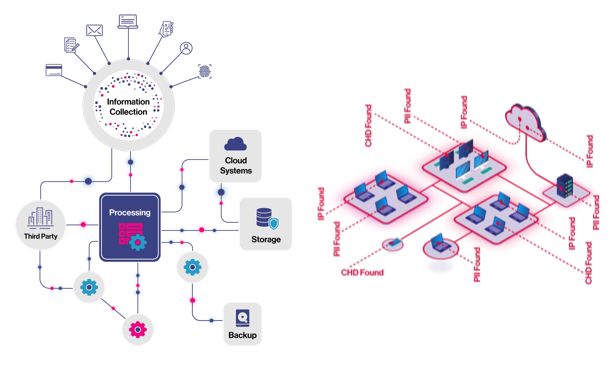
Data flows (right) show what you expect; Discovery scans (left) uncover the reality
Find out more and arrange a workshop with one of our experts at a time that suits you.

