On 1 September 2019, the updated Personal Data Protection Act (PDPA) for NRIC and other National Identification Numbers regulation will take effect, making it illegal for organizations to collect, use or disclose Singapore National Registration Identity Card (NRIC) numbers. This means that businesses will no longer be allowed to ask for an individual’s NRIC for the purpose of signing up for retail memberships, online movie ticket purchases or when submitting feedback for a new product, among other activities. While the new rules issued by the Singapore Personal Data Protection Commission (PDPC) do not apply to public agencies in Singapore (such as government ministries), NRIC numbers (or copies of NRIC cards) can only be used by organizations if required under the law, or if it’s necessary to accurately verify and identify an individual to a “high degree of fidelity.”
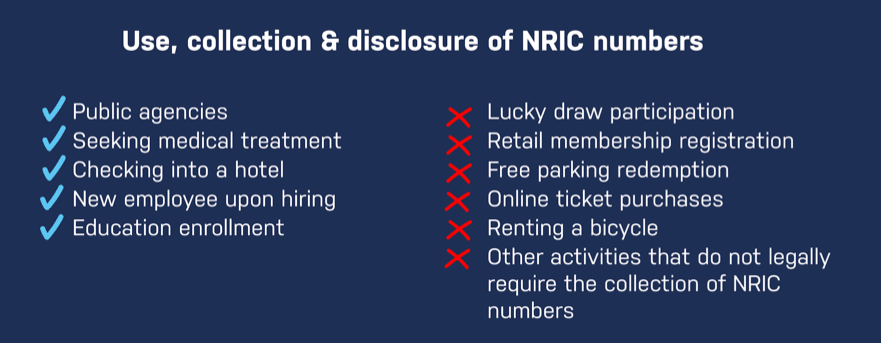
As NRIC numbers can potentially grant access to large amounts of information pertaining to an individual, the PDPC requires that organizations take reasonable measures to ensure the security and protection of personal data in its possession and control. When no longer necessary for any legal or business purposes, organizations are required to remove the personal data from their records or remove the means by which the personal data can be connected to an individual.
With the regulation’s enforcement date rapidly approaching, it’s critical for organizations to be prepared in order to maintain compliance with the updated PDPA legislation, as failure to comply could lead to fines of up to 1 million Singapore dollars.
Are You Ready to be Compliant?
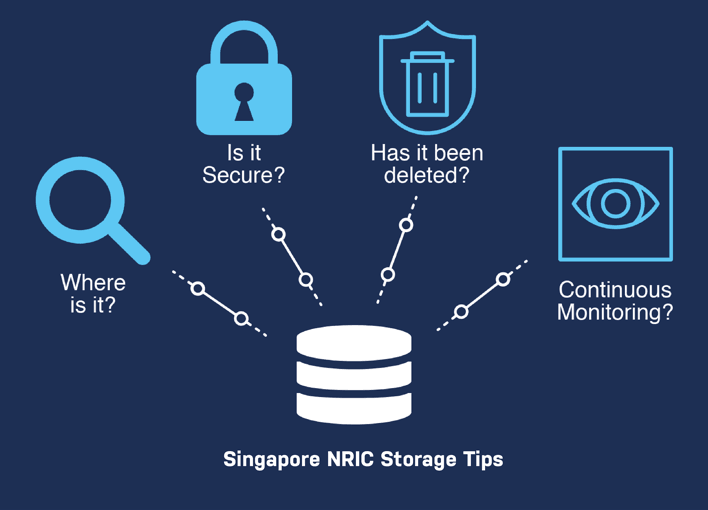
When assessing your organization’s risk under the updated PDPA guidelines relating to storage of NRIC numbers, we recommend these four simple steps:
1. Where does your sensitive data reside?
Understanding where are all the NRIC numbers are stored within your organization is step one. Sensitive Data Discovery allows organizations to understand where sensitive data lives, such as NRIC numbers, in order to allow users to secure or delete it in an effort to remain compliant. Data discovery is extremely critical when it comes to adhering to strict compliance regulations — yet a study by Gemalto [MOU1] indicates that only 54 percent of companies are actually aware of where all of its sensitive personal data is stored.
2. Is all of your sensitive data secure beyond NRIC?
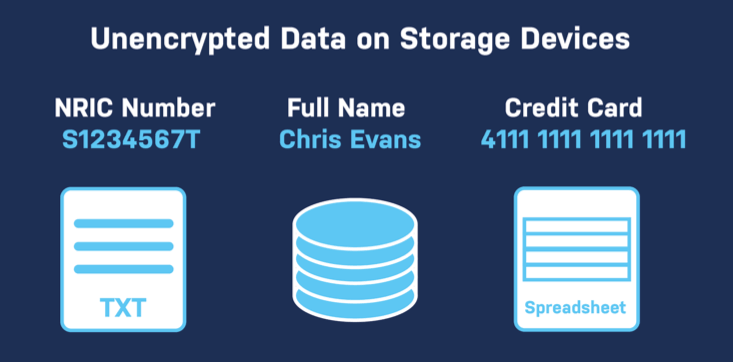
Traditionally, the most common method of storage is a text file or log file, a local file database without encryption or in some other structured data storage facility that allows the data to be stored and accessed unencrypted.
Third party vendors may pose equal, or in some cases, even higher risk when it comes to securing sensitive data. While internally, an organization may have implemented best practices for data security, this may not be the case when it comes to third party vendors and technology partners. Their internal policies may not utilize or follow the same rigorous standards applied within your organization, posing as a major security risk to sensitive data. Many organizations overcome these challenges by undergoing annual vendor revalidation exercises. This can be as simple as a detailed self-assessment questionnaire which is incorporated into your contractual agreement also requiring detailed on-site assessments by an independent security assessor.
3. Has your NRIC and related sensitive data been deleted?
Regardless of industry and how NRIC data was historically used, the best data security strategy an organization can follow is to delete the data entirely. This goes for almost any form of personal data under the PDPA, but the NRIC numbers carry the most weight and sensitivity, putting it at an increased level of priority.
If you have a clear regulatory mandated requirement to store an individual’s full NRIC number with no viable alternative, your organization bears a heavy obligation around security and ongoing protection to ensure that this data does not become subject to a data breach.
4. Are you monitoring your sensitive data continuously?
After your sensitive data cleanup is complete, the work is far from finished. Sensitive data compliance is not a destination, but rather a journey.
In all data security initiatives, the biggest failure generally occurs after the project is complete with all personnel involved moving on to other initiatives. Unless continuous monitoring to validate and ensure no new insecure NRIC data storage occurs is implemented, organizations have zero assurance that a relapse has not occurred.
These relapses often occur due to changes in organizational process or new processes being introduced, acquisitions or regular operational investigation activities such as system administrators enabling verbose debug logging when troubleshooting applications. This can often result in unexpected and unknown personal data storage.
Understanding where your data resides is the first step.
No security initiative involving the locking down or elimination of personal data can be effective or accurate without a thorough review of every single data storage point within the organization. Where traditional data security validation methods have relied upon assumption and trust of each department’s human knowledge on where data is stored, the consequences of getting this wrong are too severe in today’s threat landscape.
The only true way of identifying all Singapore NRIC and other personal data within an organization is to perform a thorough Sensitive Data Discovery process to find all personal data.
Enterprise Recon is PDPA Ready
Using Ground Labs’ Enterprise Recon software, Singapore-based companies can identify NRIC data across their entire network, whether it’s on workstations, servers, database systems, emails or cloud storage platforms such as Amazon S3 Buckets and Azure Storage.
When a scan is complete, all locations containing NRIC numbers will be displayed via the solution’s simple reporting interface.
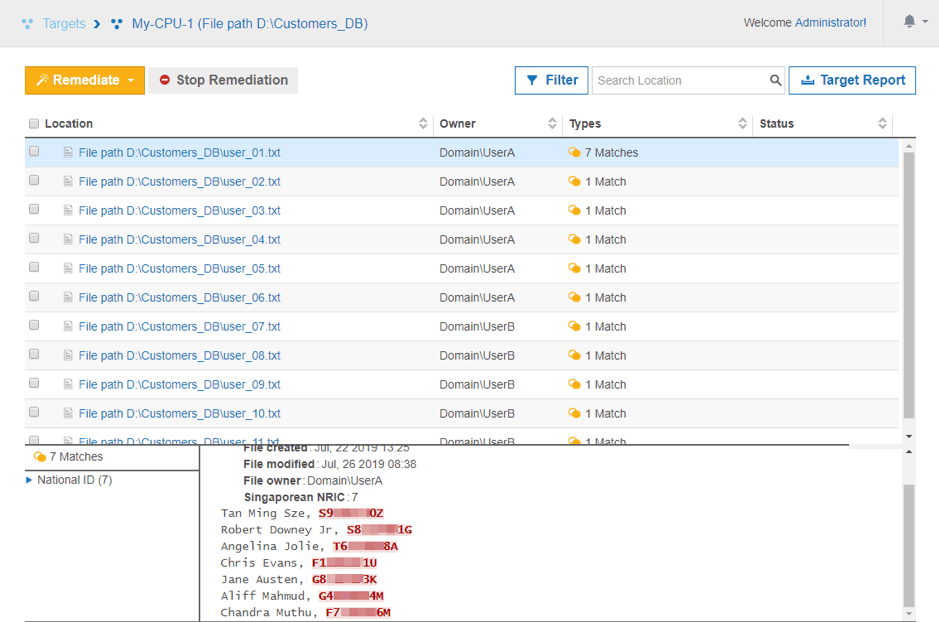
Once it’s clear where all this sensitive data resides, you can review these Singapore NRIC matches to understand which ones are still required for your organization’s business purposes. Using Enterprise Recon’s integrated remediation tools:
1.Data that needs to be kept can go through Enterprise Recon’s data masking, quarantine or encryption features ensuring that the data is secure wherever it lives and in compliance with PDPA legislation.
2. Data that must be deleted can be done so by using Enterprise Recon’s permanent deletion feature which fully eliminates file locations no matter where NRIC data has been found.
Enterprise Recon is fast and seamless to deploy, enabling organizations to set up a scan and review initial results within hours. It also supports many different platforms commonly found within businesses.
Aside from the above-mentioned Singapore NRIC numbers, the platform offers over 200 other personal data types (e.g. international passport numbers, international bank account numbers, credit card numbers, date of birth information, etc.) which can be deployed out-of-the-box. Users also have the flexibility to create custom data types to match their organization’s requirements and policies.
With Enterprise Recon, organizations can mitigate the potential costly impacts of a personal data breach by repeating four simple steps:
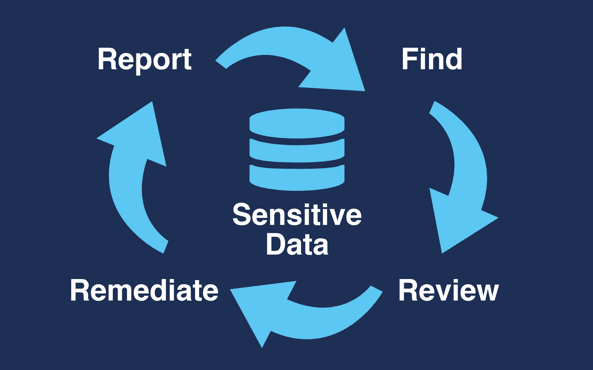
To learn how Ground Labs can help your organization achieve compliance as a “business-as-usual” process, check out the Enterprise Recon solution, or book a free demo at a time that suits you.
Ground Labs is the leading provider of sensitive data discovery solutions, enabling organizations to find, secure and remediate all of their sensitive data across multiple types and locations — whether it’s stored on-premise or in the cloud. Along with its channel partners, Ground Labs serves as the most comprehensive and trusted solution for customers to confidently mitigate risk in the face of emerging security threats and evolving compliance regulations. For more information, visit www.groundlabs.com.

