
On-demand compliance scanning
Enterprise Recon helps ensure compliance with global privacy laws, featuring 300+ preconfigured personal data types for on-demand scanning.

Rapid discovery for the data that matters
Enterprise Recon ensures fast, accurate data discovery and management with custom patterns, instant remediation, and access governance to reduce data exposure.

Bringing clarity to data management
Enterprise Recon delivers clarity to any data management strategy with comprehensive compliance reporting, data classification and advanced analytics.

Unparalleled scanning ability
Enterprise Recon offers unparalleled data discovery scanning with no impact on performance, across on-premises and cloud environments.
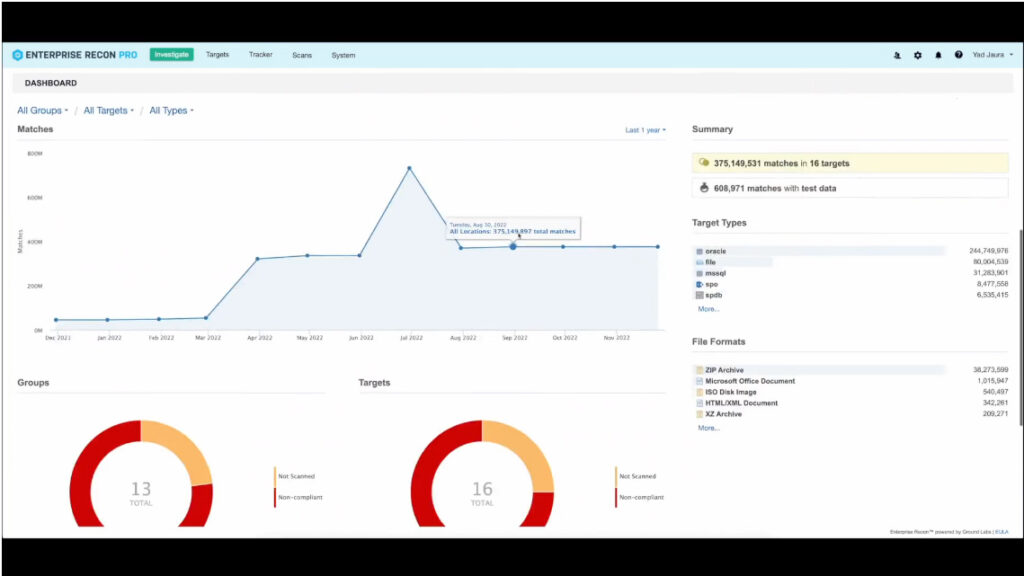
Enterprise Recon in action
Streamlined data management for privacy, security and compliance
Enterprise Recon is Ground Labs' award-winning data discovery solution packaged with on-demand remediation and data management capabilities, providing organizations maximum visibility and control of their most valuable data assets.
Thanks to its advanced discovery engine powered by GLASS Technology™, Enterprise Recon delivers scanning at scale, with lower overheads, greater accuracy and fewer false positives than other products on the market.
Companies that trust Ground Labs
Key features
On-premises data discovery
Data discovery for structured and unstructured stores of data across on-premises platforms, databases, email and archive storage
Cloud data discovery
Comprehensive cloud scanning compatible with all major cloud solutions providers, including Amazon AWS, Microsoft, Rackspace, Box and more
Rapid remediation
Instant remediation for rogue data, including redaction, secure erasure, quarantine and encryption
Data access governance
View file access restrictions identifying users or groups and level of access, and revoke unauthorized access
Data classification
Integrate with Microsoft Purview to apply data classification as persistent metadata, supporting more effective data loss prevention
Data security management
Discover where sensitive data is and who has access to it, and investigate the security posture of host systems
Data risk mapping
Apply risk scoring to discovery scan data, enabling risk profiling and prioritization for remediation and data management
Advanced business intelligence
Easy integration with ODBC-compatible applications and business intelligence platforms, for detailed data analytics

Market-leading data discovery for PCI DSS scoping and remediation

Targeted discovery, remediation and management solution for privacy and compliance

Enhanced visibility and integration capabilities offering streamlined data management for all critical data
Deploying Enterprise Recon
Our award-winning data discovery and data management solution is now available on AWS Marketplace
Enterprise Recon
Deploy a server-based installation of our industry-leading data discovery solution. Identify and manage sensitive information across on-prem and hybrid environments. Mitigate the risk of data breaches and ensure robust compliance and security at scale.
Enterprise Recon Cloud
Leverage our award-winning data discovery solution hosted in your own AWS instance. Identify and manage sensitive data across your cloud environments. Mitigate the risk of data breaches and ensure robust compliance and security at scale.
Find out how much data your organization holds with our free data sizing calculator
Licensing for Enterprise Recon is based on the total volume of data you want to scan for sensitive data and critical information.
The data calculator is for estimation purposes only. Estimates are not a quote for services, offer or contract on behalf of Ground Labs.

Check out your data volumes with our simple to use data calculator.
Data made visible with GLASS Technology™
GLASS Technology™ is the quickest and most accurate discovery software on the market, enabling rapid data discovery, risk scoring, data classification and remediation-in-place across the broadest set of platforms.
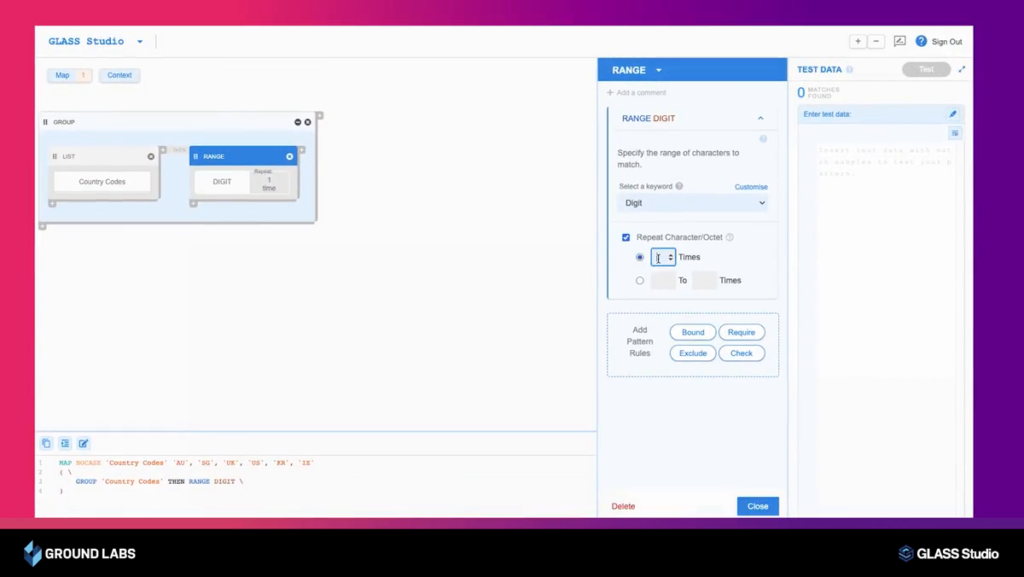
Introducing GLASS Studio™

Getting started with custom data types just got easier with GLASS Studio™
Now available for Enterprise Recon PII and Enterprise Recon Pro, GLASS Studio provides an intuitive interface for building custom data types enabling discovery of all proprietary and non-standard critical and sensitive data.
Using a guided visual builder, GLASS Studio offers a no-code alternative for rapid deployment of bespoke data patterns, complete with pattern templates and an instant test feature to ensure accurate and error-free customization.
Compare editions
| Key feature differences |  |  |  | |
|---|---|---|---|---|
| Deployment | Appliance, server and cloud deployment options | |||
| Pre-configured agents | ER Cloud | ER Cloud | ER Cloud | |
| Data patterns | Cardholder data discovery for PCI DSS | |||
| PII data discovery for privacy compliance* | ||||
| Customizable data patterns | ||||
| GLASS Studio™ | ||||
| Platform scanning | Agent, agentless and distributed scanning | |||
| On-premises and cloud scanning | ||||
| Broad platform coverage** | ||||
| Full file scanning | ||||
| Structured and unstructured data scanning | ||||
| OCR, image and audio scanning | ||||
| In-memory scanning | ||||
| Remediation | In situ data remediation | |||
| Delegated remediation | ||||
| Data access management | ||||
| Reporting | Single and multi-scan reporting | |||
| Investigate page for deeper analysis | ||||
| Data management | Data classification with MS Purview | |||
| Risk scoring and labeling | ||||
| ODBC integration with PowerBI, Tableau and more | ||||
| Administration | Role-based access control (RBAC) | |||
| Customizable notifications and alerts | ||||
| Rest API for automated access | ||||
| Support | Installation assistance | |||
| Online knowledgebase | ||||
| Email, telephone and video support | ||||
| Complimentary proof-of-concept | ||||
* click to view the full list of pre-configured PII data types
** click to view the full list of supported platforms
The latest from Ground Labs

World Password Day | Why secrets discovery is the first step to securing your organization
Have you ever counted how many times a day you access information by logging into a platform or system, or providing a password or keycode? In today’s digital world, passwords have become cemented in our personal and professional lives. The first Thursday of May is World Password Day, initiated in 2013 by Intel to raise…

Seven steps to effective data risk management
Data risk management is becoming increasingly important to businesses, as the vast amounts of data generated today present potential both for operational gain and organizational risk. Over the last decade, data has emerged as the lifeblood of innovation. Nevertheless, handling such vast quantities of data, much of which is personal or commercially sensitive, comes with…

DeepSeek, GenAI and data sovereignty: What privacy professionals need to know
When DeepSeek was released in January, it caused shockwaves in international stock markets and became the most downloaded app across Apple and Google app stores. The instant success of the application has sparked significant debate — not for its features or capabilities, but for the questions it raises about data sovereignty. This concern is not…

Meeting the challenge of 4.0.1 — Highlights from the 26th PCI London
The 26th PCI London, held on January 21, 2025, at the Park Plaza in Victoria, brought together cybersecurity experts, IT professionals and organizations to discuss the evolving world of PCI DSS compliance and cybersecurity strategies. Industry leaders shared insights on the latest PCI security standards updates, their challenges and best practices for safeguarding cardholder data…

Building trust in digital transactions: Payment security in 2025
The payment landscape continues evolving rapidly, influenced by technological advancements and changing consumer behaviors. These changes present new threats to payments security and demand flexibility and innovation to ensure continued consumer trust. This article explores the key trends shaping payment security in 2025. From advanced threat intelligence and biometrics to AI-driven fraud detection and API…








