Introducing Data Security Posture Management (DSPM)
Modern businesses are generating, storing and processing more information across more diverse environments than ever before. This trend is set to continue as organizations embrace AI technologies and reject traditional on-premises operations for the agility and feature-rich offerings of cloud-based networks and SaaS platforms.
However, this vast opportunity also brings its own unique set of risks – data breaches, regulatory non-compliance and insider threats are more prevalent than ever. The geopolitical climate and the nation-state threat is driving concern around data sovereignty and the need for organizational control over sensitive data assets.
To address these challenges, a new category of data-first cybersecurity has emerged: Data Security Posture Management (DSPM).
DSPM is a proactive, data-centric approach to identifying, managing and securing sensitive data across an organization’s entire digital estate. It provides visibility into where sensitive data resides, who has access to it, how it is being used and whether it is adequately protected.
This article will explore what DSPM is, why it's important and how Ground Labs' Enterprise Recon supports effective DSPM implementation.
Gartner’s definition of DSPM
DSPM was originally coined by Gartner in a 2023 Insight Innovation report.
According to Gartner, DSPM technologies are designed to:
“Provide visibility as to where sensitive data is, who has access to that data, how it has been used, and what the security posture of the data stored or application is. It does that by assessing the current state of data security, identifying and classifying potential risks and vulnerabilities, implementing security controls to mitigate these risks, and regularly monitoring and updating the security posture to ensure it remains effective.”
Gartner emphasizes that DSPM is not just about visibility of data – it’s about enabling security and risk leaders to take control of their data security strategy by integrating DSPM into broader data governance and cybersecurity frameworks.
According to Gartner, by 2026, more than 20% of organizations will deploy DSPM technology, due to the “urgent requirements to identify and locate previously unknown data repositories and to mitigate associated security and privacy risks.”
Why Data Security Posture Management matters
The core objective of Data Security Posture Management is to continuously assess and improve the security posture of sensitive data. Unlike traditional security models that focus on infrastructure or perimeter defenses, DSPM shifts the focus directly to the data itself – ensuring that it is discovered, classified, monitored and protected – regardless of where it lives.
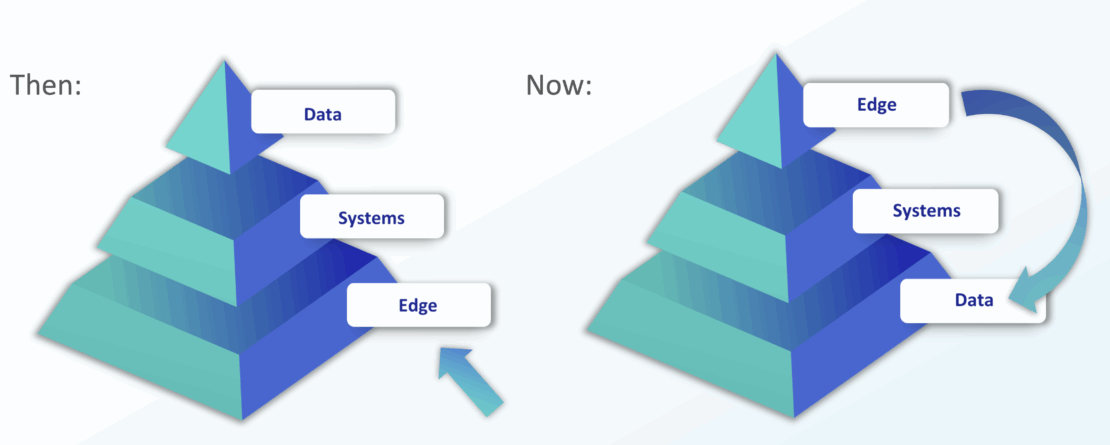
According to IBM, 35% of data breaches affected “shadow data” stores in 2024 – unknown data repositories within an organization's digital estate. Further, shadow data theft resulted in a 16% greater cost of a breach – $5.27m for a shadow data breach, compared to the average breach cost of $4.88m.
However, not all shadow data is located in cloud and SaaS environments. IBM reported that 25% of breaches involving shadow data were solely on-premises incidents.
These incidents highlight the critical role of DSPM across all network environments as an exhaustive, multi-environment approach to data security.
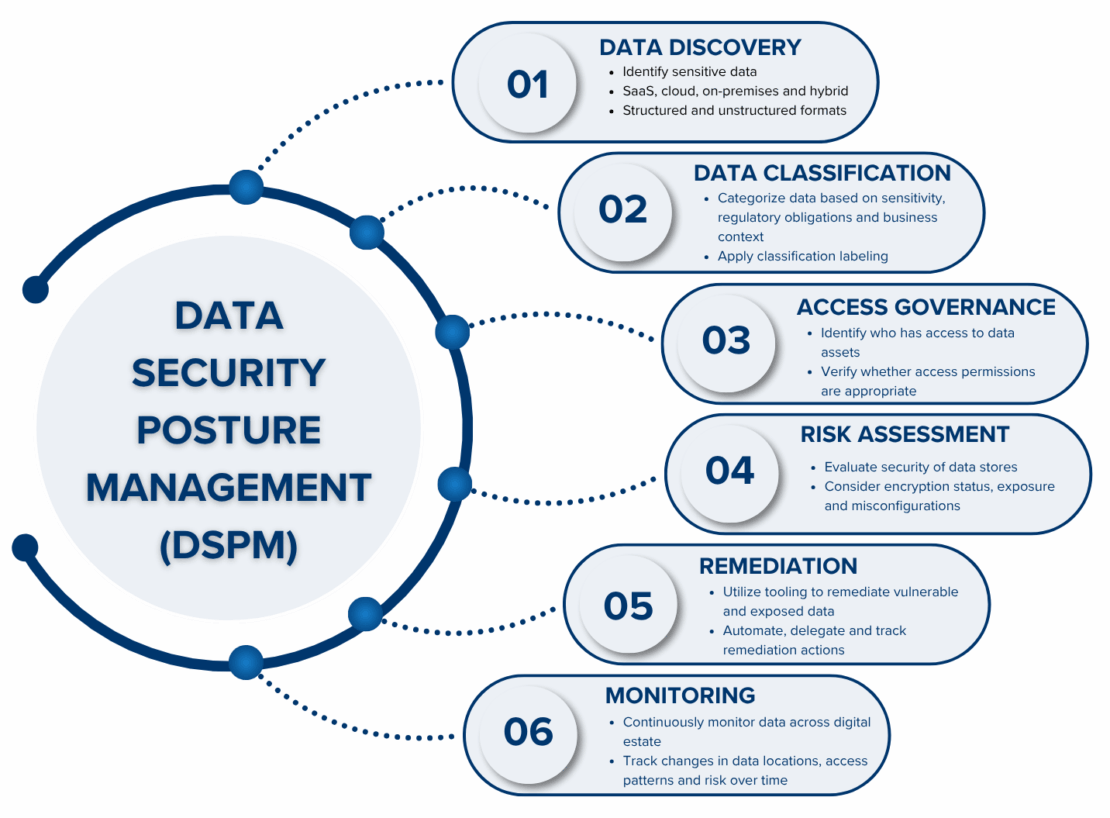
Essential components of DSPM
A robust DSPM solution must deliver the following essential components:
- Data discovery: Automatically locate structured and unstructured sensitive data across SaaS, cloud, on-premises and hybrid environments. Scan across databases, file systems, cloud storage, SaaS platforms, and endpoints. Identify all sensitive data assets, including shadow and orphaned data.
- Data classification: Categorize data based on sensitivity, regulatory requirements and business context. This should include PII, ePHI, cardholder data, intellectual property and other sensitive data types. Apply classification labeling or tags to data assets.
- Access governance: Identify who has access to sensitive data and whether that access is appropriate. Evaluate user groups with access to data repositories, based on the types of data stored. Revoke inappropriate, unused or risky permissions.
- Risk assessment: Evaluate the security posture of data, including encryption status, exposure, platform vulnerabilities and misconfigurations. Define data risk profiles based on its sensitivity and classification.
- Remediation: Utilize tooling to remediate vulnerable and exposed data through encryption, quarantine, masking or deletion. Automate, delegate and track remediation actions to address policy violations and security risks.
- Continuous monitoring: Track changes in data location, access patterns and risk levels over time. Regularly monitor for new shadow data stores.
How Enterprise Recon supports DSPM
Enterprise Recon by Ground Labs is a powerful data discovery and classification platform that aligns closely with the principles of DSPM.
- Sensitive data discovery: Enterprise Recon delivers fast, accurate scanning for identifying sensitive data in both structured and unstructured formats, across on-premises and cloud systems. It is preconfigured with 300+ personal data types including ePHI and cardholder data for PCI DSS. Meanwhile, custom data types can be used to detect various types of secrets, including passwords, API keys, tokens, SSH keys and private certificates.
- Data classification: Enterprise Recon integrates with Microsoft Purview to apply data classification as persistent metadata, supporting effective labelling for data loss prevention and risk assessment
- Access governance: Enterprise Recon Pro offers data access management features, providing visibility into access permissions for identified data assets and allowing user-group-level modifications to restrict access where required
- Risk assessment: Enterprise Recon enables risk scoring of discovery scan data, enabling risk profiling and prioritization for remediation and continuous risk monitoring
- Remediation: Enterprise Recon supports instant remediation of exposed or vulnerable data through encryption, quarantine, masking/truncation and deletion. Delegated remediation features enable actions to be managed by data owners and tracked to completion.
- Continuous monitoring: Enterprise Recon can be used to automate the process of discovery and data management, with frequent scanning to continuously monitor the data environment and support effective DSPM.
Adopt DSPM with Ground Labs
Data Security Posture Management is a critical evolution in data security, offering organizations the tools and insights needed to protect sensitive data in an increasingly complex digital landscape. By aligning with Gartner’s vision and implementing solutions like Ground Labs’ Enterprise Recon, organizations can build a resilient, data-centric security posture that meets today’s regulatory and operational demands.
Need help getting started with DSPM? Arrange your complimentary data risk assessment or book a call with one of our experts today.
