Organizations today must prioritize cybersecurity to protect themselves in the face of an ever increasing barrage of cyber-threats. Whether this comes from cybercriminals seeking data for sale or extortion or to cause disruption, or from internal sources including disgruntled staff members and trusted suppliers – data is the primary target.
As organizations generate and store more information than ever before, the ability to understand, manage and protect that data is the foundation of effective cybersecurity.
In this post, we explain how data discovery supports common cybersecurity frameworks and standards, as well as compliance with global laws and regulations, and facilitates security controls including zero-trust, identity and access management (IAM) and data loss prevention (DLP).
Cybersecurity in a time of complexity and change
The global cybersecurity landscape in 2025 is marked by escalating complexity, driven by increasingly sophisticated cyber threats, geopolitical tensions and the rapid evolution of technologies such as AI and quantum computing.
Organizations now operate in highly fragmented digital environments composed of multiple cloud services, SaaS platforms and third-party supply chains, and a hybrid workforce spanning on-premises and remote locations. This distributed architecture significantly expands the attack surface, making traditional perimeter-based security models obsolete.
At the same time, regulatory frameworks and security standards are tightening worldwide, with sweeping changes such as the EU’s Digital Operational Resilience Act (DORA) and updates to standards like NIST CSF and PCI DSS. These regulations demand greater accountability, resilience and transparency, driving organizations to adopt more integrated and proactive cybersecurity strategies to remain compliant and secure.
The role of data discovery in cybersecurity
Effective cybersecurity begins with understanding what data exists, where it resides and how it flows through an organization’s digital environment from capture to deletion.
Data discovery is crucial to this process, enabling organizations to locate sensitive, regulated and business-critical information across diverse formats and environments – from structured databases to unstructured files and semi-structured logs. This visibility is critical not only for reducing risk – especially as 1 in 3 breaches now involve shadow data – but also for meeting growing regulatory demands.
The most commonly breached data types globally in 2024 were personally identifiable information (PII), electronic protected health information (ePHI) and authentication credentials. In the UK alone, half of businesses and nearly a third of charities reported experiencing a cybersecurity breach or attack in 2023/24.
Alarmingly, in 2025 there was a 58% surge in infostealer attacks targeting authentication credentials. This is a growing risk to organizations, as identity-based attacks made up 30% of all intrusions in 2024. These attacks are harder to spot, taking longer to respond and contain, because they originate from an authenticated source. As a consequence, secrets discovery is becoming an essential part of cybersecurity, currently overlooked by many businesses.
Further, data discovery enables robust data governance and auditability and supports incident response and business resilience – as well as the identification and remediation of at-risk data – ultimately forming the backbone of a robust cybersecurity posture.
Data discovery and cybersecurity standards
Over the last five years, cybersecurity standards have evolved amid the shifting cybersecurity threat landscape. Perimeter-led, network-based security practices are no longer effective, and instead good security practices now adopt a data-centric approach.
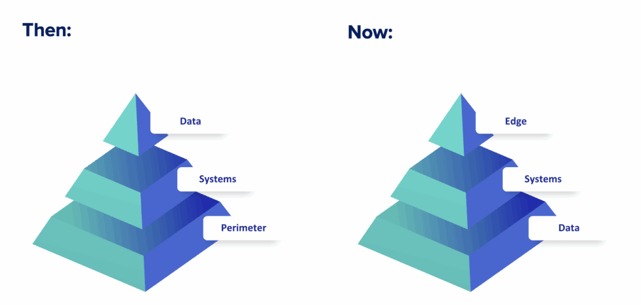
ISO27001:2022 requires that “An inventory of information and other associated assets, including owners, shall be developed and maintained” (A5.9). In previous versions, this was focused towards information systems rather than the data itself.
NIST CSF 2.0 includes several requirements directly supported by data discovery tools, specifically:
- ID.AM-03 Representations of the organization’s authorized network communication and internal and external network data flows are maintained
- ID.AM-07 Inventories of data and corresponding metadata for designated data types are maintained
Meanwhile, the CSF implementation examples explain that businesses must “continuously discover and analyze ad hoc data” to identify new instances of sensitive data.
The CIS Critical Security Control framework breaks asset identification into three separate controls; enterprise assets, software assets and data protection. Data protection includes, “processes and technical controls to identify, classify, securely handle, retain, and dispose of data.”
These data-first approaches are echoed in standards and privacy compliance frameworks, laws and regulations including PCI DSS, HIPAA, GDPR and more.
Cybersecurity foundations built on data visibility
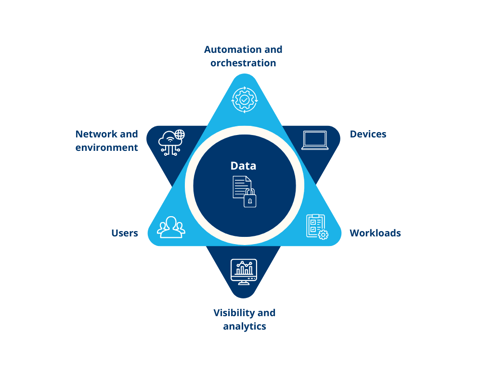
Beyond direct capabilities to discover and remediate vulnerable data, purpose-built data discovery and data management solutions also support foundational controls for effective cybersecurity, including zero-trust, IAM and DLP.
Zero-trust
The core principle of zero-trust is "never trust, always verify." This approach presumes that threats can originate from within or outside traditional network boundaries. It mandates rigorous identity verification for every individual and device attempting to access company resources including data and systems, irrespective of their location.
To effectively implement zero-trust, organizations must first identify their data across all network locations, cloud and SaaS platforms, then assess and categorize it by sensitivity and criticality.
As zero-trust environments mature, continuous automated discovery and tracking is essential for identifying and classifying data assets to maintain an accurate resource inventory. As CISA's Zero Trust Maturity Model explains, this inventory should encompass all structured and unstructured files and data fragments across every system type and location, along with their associated metadata.
Identity and access management (IAM)
Identity and access management (IAM) encompasses the processes, policies and technologies used to manage digital identities and control user access to organizational resources. Its primary goal is to ensure that only authorized individuals can access specific systems and data – only when necessary and for approved purposes.
Effective IAM depends on accurate, up-to-date information about users, systems, and data resources to assign access rights appropriately.
Data discovery plays a critical role in IAM by identifying sensitive information across internal systems, cloud and SaaS platforms, and collaboration tools on an ongoing basis. Some advanced tools go further by providing visibility into access permissions and enabling immediate revocation of unauthorized access. This ensures that access controls are consistently applied to all sensitive and high-risk data assets.
Data loss prevention (DLP)
Data discovery and data loss prevention (DLP) work hand in hand to help organizations identify and protect sensitive information. Data discovery is a prerequisite for effective DLP, since DLP relies on the accurate and comprehensive classification of data.
To ensure a DLP system operates at its full potential, data discovery needs to be implemented as a continuous process. Regular scans help ensure the identification and labelling of new data as it is created or captured. This ongoing visibility enables DLP tools to enforce policies accurately and respond swiftly to potential threats.
How Enterprise Recon supports cybersecurity
Enterprise Recon delivers automated data discovery across an organization’s entire digital ecosystem. It enables security teams to locate and classify sensitive data – such as PII, ePHI and authentication credentials – across structured and unstructured sources, including cloud platforms and legacy systems.
This comprehensive visibility enables organizations to proactively identify all information assets, remediate vulnerable data and apply appropriate security controls. The enhanced visibility of data Enterprise Recon delivers further supports zero-trust implementation, enhances IAM and ensures all sensitive data is identified, classified and labeled for effective DLP.
Future-proofing cybersecurity with a data-centric approach
As cyber threats evolve and regulatory demands intensify, organizations must adopt a proactive, data-first approach to security. Data discovery is no longer optional – it is foundational.
By leveraging advanced tools like Enterprise Recon, businesses can gain the visibility and control they need to protect sensitive information, support compliance and build a resilient cybersecurity posture.
Ultimately, securing data is securing the organization itself.
To find out how Ground Labs can support your business, arrange a complimentary data workshop or book a call with one of our experts today.




