Enterprise Recon 2.2
Exchange Online
To continue scanning Exchange Online without interruption, add the Exchange Online Target, which is available from ER 2.1.
This section covers the following topics:
Exchange Online
When Exchange Online is added as a scan Target, ER2 returns all Microsoft 365 groups and user accounts with active mailboxes in each group. You can select specific groups or individual users when setting up the scan schedule, and each group will be presented as a separate location for the Exchange Online Target.
Here are some scenarios which may benefit from scanning Exchange Online mailboxes by Microsoft 365 groups:
- Users in the organization are typically managed as groups, and assigned group memberships in your Microsoft 365 environment.
- Compliance procedures requires the capability to segregate and report scan results by business unit, division or group.
- Head of Departments are only authorized to review and remediate non-compliant mailboxes in certain groups. This can be easily managed by delegating specific Resource Permissions to the user.
You can also scan all users with mailboxes in your organization's domain by adding the "All Users" group as a scan location.
Example of Exchange Online structure:
Exchange Online [domain: example.onmicrosoft.com]
+- Exchange Online on target EXCHANGEONLINE:EXAMPLE.ONMICROSOFT.COM
+- Group All Users
+- Group Engineering
+- Group Design
Licensing
For Sitewide Licenses, all scanned Exchange Online Targets consume data from the Sitewide License data allowance limit.
For Non-Sitewide Licenses, Exchange Online Targets require Client Licenses, and consume data from the Client License data allowance limit.
See Target Licenses for more information.
Requirements
| Requirements | Description |
|---|---|
| Proxy Agent |
|
| TCP Allowed Connections | Port 443 |
Configure Microsoft 365 Account
For ER 2.1 and above, you will need to perform the following setup to scan Exchange Online Targets:
Generate Client ID and Tenant ID Key
- With your administrator account, log into the Azure app registration portal.
- In the App registrations page, click on + New registration.
-
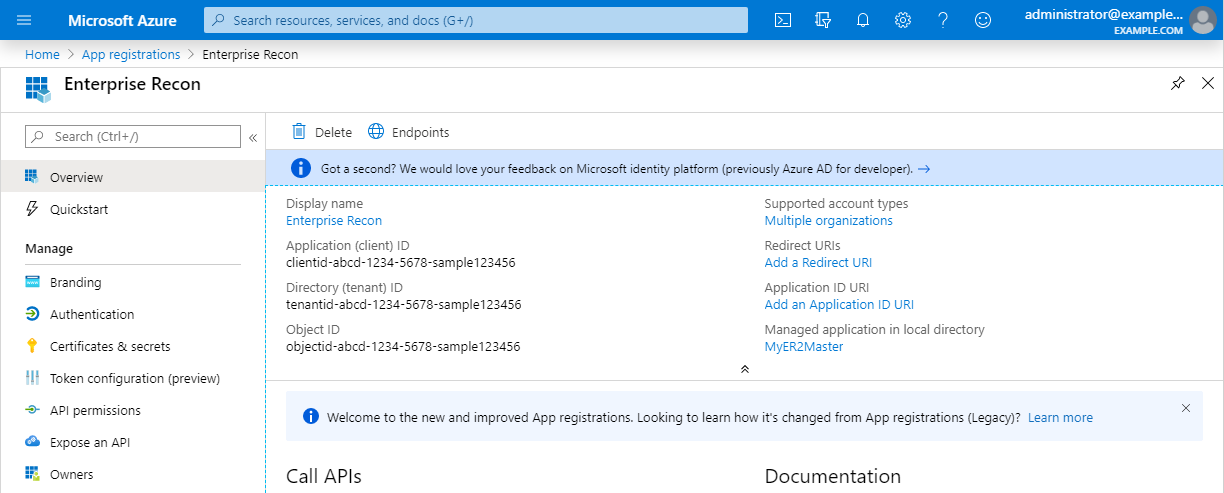
In the Register an application page, fill in the following fields:
Field Description Name Enter a descriptive display name for ER2. For example, Enterprise Recon. Supported account types Select Accounts in this organizational directory only. - Click Register. A dialog box appears, displaying the overview for the newly registered app, "Enterprise Recon".
-
Take down the values for the Application (client) ID and Directory (tenant) ID. This will be required when you Set Up Exchange Online as a Target Location.
Generate Client Secret Key
- With your administrator account, log into the Azure app registration portal.
- In the App registrations page, go to the Owner applications tab. Click on the app that you registered when generating the Client ID and Tenant ID key. For example, "Enterprise Recon".
- In the Manage panel, click Certificates & secrets.
- In the Client secrets section, click + New client secret.
-
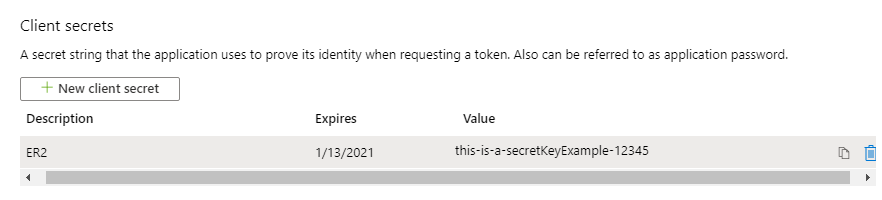
In the Add a client secret page, fill in the following fields:
Field Description Description Enter a descriptive label for the Client Secret key. Expires Select a validity period for the Client Secret key. - Click Add. The Value column will contain the Client Secret key.
-
Copy and save the Client Secret key to a secure location. This will be required when you Set Up Exchange Online as a Target Location.
Save your Client Secret key in a secure location. You cannot access this Client Secret key once you navigate away from the page.
Grant API Access
To scan Exchange Online Targets, you will need to grant ER2 permissions to access specific resource APIs.
- With your administrator account, log into the Azure app registration portal.
- In the App registrations page, go to the Owner applications tab. Click on the app that you registered when generating the Client ID and Tenant ID key. For example, "Enterprise Recon".
- In the Manage panel, click API permissions.
- In the Configured permissions section, click + Add a permission.
- In the Request API permissions page, select Microsoft Graph > Application permissions.
-
Select the following permissions for the "Enterprise Recon" app:
API Permissions Description - Group.Read.All
- User.Read.All
- Directory.Read.All
- Mail.Read
- Contacts.Read
- Calendars.Read
Required for probing and scanning Exchange Online Targets. - Group.ReadWrite.All
- User.ReadWrite.All
- Directory.ReadWrite.All
- Mail.ReadWrite
- Contacts.ReadWrite
- Calendars.ReadWrite
Required for remediating Exchange Online Targets. - Click Add permissions.
- In the Configured permissions page, click on Grant admin consent for <organization name>.
- In the Permissions requested Accept for your organization window, click Accept. The Status column for all the newly added API permissions will be updated to "Granted for <organization name>".
Set Up Exchange Online as a Target Location
This section describes how to set up Exchange Online Targets for ER 2.1 and above.
- Configure Microsoft 365 Account.
- From the New Scan page, Add Targets.
- In the Select Target Type dialog box, select Microsoft 365 > Exchange Online.
- Fill in the following details:
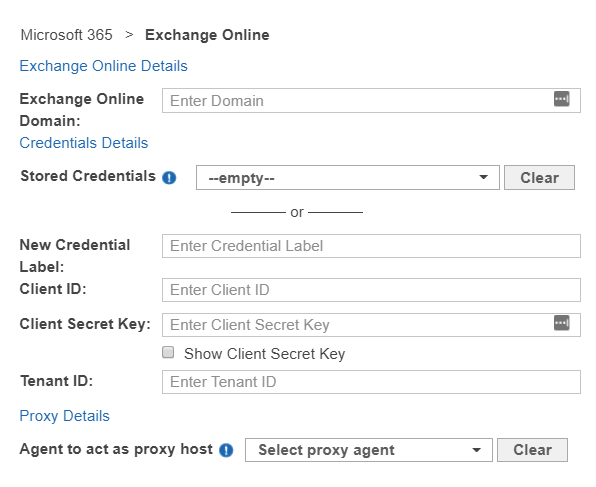
Field Description Microsoft 365 Domain Enter your Microsoft 365 domain name.
To scan the mailbox of a specific Microsoft 365 group or user account, see Edit Exchange Online Target Path.New Credential Label Enter a descriptive label for the credential set. Client ID Enter the Client ID. See Generate Client ID and Tenant ID Key for more information. Client Secret Enter the Client Secret key. See Generate Client Secret Key for more information. Tenant ID Enter the Tenant ID. See Generate Client ID and Tenant ID Key for more information. Agent to act as proxy host Select a Proxy Agent host with direct Internet access. - Click Test. If ER2 can connect to the Target, the button changes to a Commit button.
- Click Commit to add the Target.
- Back in the New Scan page, locate the newly added Exchange Online Target and click on the arrow next to it to display a list of available Microsoft 365 groups for the domain.
- Select the Target location(s) to scan:
-
If "All Users" is selected, ER2 scans all user accounts in the Microsoft 365 domain.
"All Users" is a default, non-configurable virtual group in ER2 that automatically includes all user accounts in the Microsoft 365 domain. If a similar "All Users" group pre-exists in your Microsoft 365 environment, we recommend that you change the display name for that group as it will be viewed as a duplicate group and will not be displayed in ER2. -
If only specific groups are selected, ER2 only scans user accounts in the selected groups.
-
- Click Next to continue configuring your new scan.
Edit Exchange Online Target Path
- Set Up Exchange Online as a Target Location.
- In the Select Locations section, select your Exchange Online Target location and click Edit.
- In the Edit Exchange Online dialog box, enter a Path to scan. Use the
following syntax:
Mailbox / Folder to Scan Path All user accounts in a specific group Syntax: <Group Display Name>
Example: Engineering (SG)
Specific user account in group Syntax: <Group Display Name>/<User Principal Name>
Example: Engineering (SG)/user1@example.com
Specific folder for user account in group Syntax: <Group Display Name>/<User Principal Name>/<Mailbox Folder>
Example: Engineering (SG)/user1@example.com/ProjectA
All user accounts Syntax: All Users
Specific user account Recommended for scanning mailboxes of user accounts that do not belong to any Microsoft 365 group.Syntax: All Users/<User Principal Name>
Example: All Users/user1@example.com
Specific folder for user account Recommended for scanning mailboxes of user accounts that do not belong to any Microsoft 365 group.Syntax: All Users/<User Principal Name>/<Mailbox Folder>
Example: All Users/user1@example.com/ProjectA
If there are multiple Microsoft 365 groups with the same display name in your domain, ER2 will only retrieve the first group occurrence. For example, if there are three groups with the same display name, "Engineering", ER2 will only probe, scan and return results for the first "Engineering" group for the Exchange Online Target. - Click Test and then Commit to save the path to the Target location.
Unsupported Mailbox Types and Folders
ER2 currently does not support the following mailbox types and folders for the Exchange Online Target:
- Archived mailboxes (In-Place Archives)
- Disabled mailboxes
- Deleted mailboxes
- Inactive mailboxes
- Shared mailboxes (unlicensed)
- Microsoft 365 Group mailboxes and conversations
Mailbox in Multiple Groups
This section describes the behavior of mailboxes that are members of multiple groups for the Exchange Online Target.
License Consumption
A mailbox for a user account that belongs to multiple groups
- is scanned each time a group the user belongs to is scanned.
- consumes only 1x data allowance usage regardless of how many times it is scanned as part of different groups.
When both "Engineering" and "Design" groups are added to the same scan, the mailbox for "UserA" is scanned once when "Engineering" is scanned, and a second time when "Design" is scanned.
Mailbox for "UserA" consumes only one Client License, and 5 MB Client License data allowance despite having been scanned twice.
Scan Results
Matches that are found in mailboxes that belong to multiple groups will be reported as a distinct match count for each group.
Take for example a simplified Exchange Online Target for the domain "example.onmicrosoft.com" below:
EXAMPLE.ONMICROSOFT.COM 55 matches
+– Engineering 30 matches
+– UserA 10 matches
+– UserB 20 matches
+– Design 25 matches
+– UserA 10 matches
+– UserC 15 matches
Matches found in the mailbox for UserA will be included in the match count for both Engineering and Design groups.
Exchange Online (EWS)
To continue scanning Exchange Online without interruption, add the Exchange Online Target, which is available from ER 2.1.
Licensing
For Sitewide Licenses, all scanned Exchange Online (EWS) Targets consume data from the Sitewide License data allowance limit.
For Non-Sitewide Licenses, Exchange Online (EWS) Targets require Client Licenses, and consume data from the Client License data allowance limit.
See Target Licenses for more information.
Requirements
| Requirements | Description |
|---|---|
| Proxy Agent |
|
| TCP Allowed Connections | Port 443 |
Enable Impersonation in Microsoft 365
To scan Exchange Online (EWS) Targets, use a service account assigned with the ApplicationImpersonation and Mailbox Search roles:
- Log into your Microsoft 365 global administrator account.
- Create a new service account for use with ER2.
Service Accounts
Service accounts are user accounts set up to perform administrative tasks only. Because of the broad permissions granted to service accounts, we recommend that you closely monitor and limit access to these accounts.
Exchange Online (EWS) Licenses
Exchange Online (EWS) does not usually require you to assign a Microsoft 365 license to the service account used to scan mailboxes. - We need a custom admin role to assign the service account to. To create a
custom admin role:
- Navigate to the Exchange admin center by going to ADMIN > Exchange.
- In the Exchange admin center, select permissions and go to the admin roles tab.
- In the roles tab, click +.
- This brings up the Role Group page. Configure the custom admin role:
- Under the Roles section, select the ApplicationImpersonation and Mailbox Search roles.
- Add the service account created in step 2 to the list of Members, or users that are assigned this custom admin role.
- Click Save.
Set Up Exchange Online (EWS) as a Target Location
- Enable Impersonation in Microsoft 365.
- From the New Scan page, Add Targets.
- In the Select Target Type dialog box, select Microsoft 365 > Exchange Online (EWS).
-
Fill in the following details:
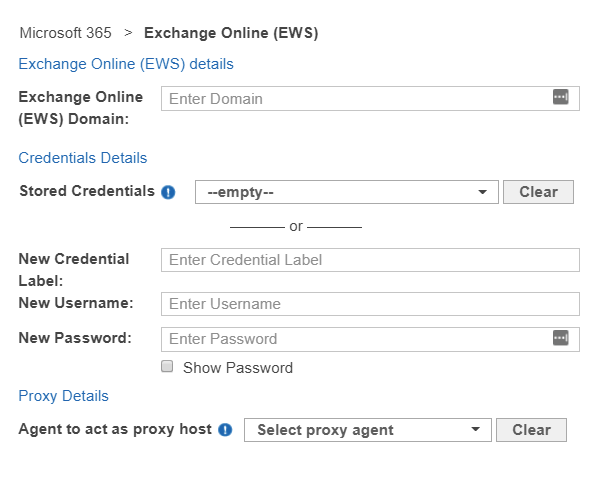
Field Description Microsoft 365 Domain Enter your Microsoft 365 domain name.
To scan the mailbox of a specific Microsoft 365 user account, see Edit Exchange Online (EWS) Target Path.New Credential Label Enter a descriptive label for the credential set. New Username Enter the service account user name. See Enable Impersonation in Microsoft 365 for more information. New Password Enter your service account password. Agent to act as proxy host Select a Proxy Agent host with direct Internet access. - Click Test. If ER2 can connect to the Target, the button changes to a Commit button.
- Click Commit to add the Target.
Edit Exchange Online (EWS) Target Path
- Set Up Exchange Online (EWS) as a Target Location.
- In the Select Locations section, select your Exchange Online (EWS) Target location and click Edit.
-
In the Edit Exchange Online (EWS) dialog box, enter a Path to scan. Use the following syntax:
Path Syntax Specific user account <User Display Name> - Click Test and then Commit to save the path to the Target location.