Enterprise Recon 2.3
Enable HTTPS
This section covers the following topics:
- Enable HTTPS
- Automatic Redirects to HTTPS
- Custom SSL Certificates
- Obtain Signed SSL Certificate
- Install the New SSL Certificate
- Add Certificate as Trusted Certificate Authority
- Restart the Web Console
- Self-Signed Certificates
Enable HTTPS
If a valid SSL certificate has been installed on the Master Server, you will be automatically redirected to the HTTPS site when connected to the Web Console. See Automatic Redirects to HTTPS for more information.
To manually navigate to the HTTPS site, include https:// when entering the IP address, host name, or domain name with which you access the Web Console.
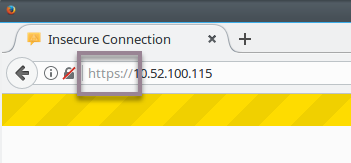
Your browser warns that the Web Console "uses an invalid security certificate". This is the self-signed SSL certificate that the Master Server generates on installation. Most browsers correctly treat self-signed certificates as invalid, but will allow security exceptions to be added.
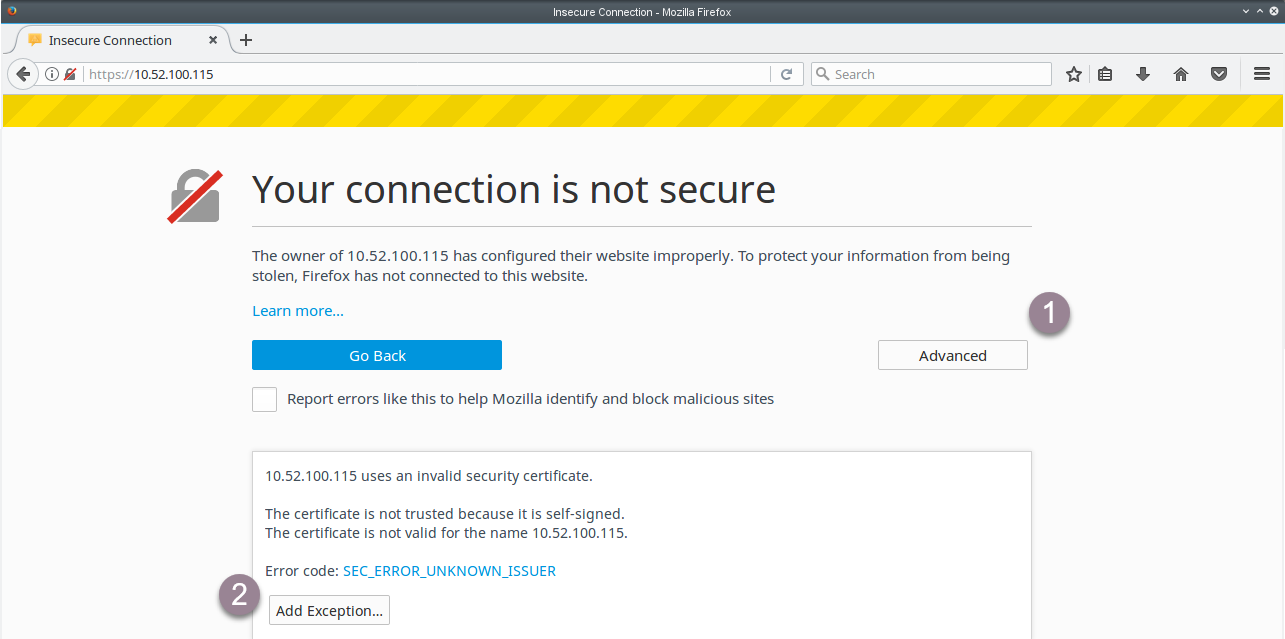
To force the browser to use HTTPS to connect to the Web Console, ask the browser to ignore the SSL certificate warning and to add a security exception when prompted:
- In your browser, click Advanced.
- Click Add Exception.
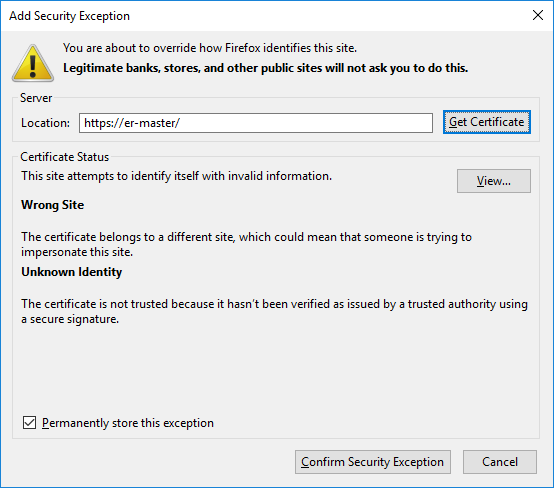
- In the Add Security Exception dialog box:
- Click Confirm Security Exception to proceed to the HTTPS site.
- Select Permanently store this exception to prevent your browser from displaying this warning for the Web Console again.
Automatic Redirects to HTTPS
To have the Web Console automatically redirect users to the HTTPS site, update the Master Server with a custom SSL certificate.
Custom SSL Certificates
To prevent your browser from displaying the security certificate warning when connecting to the Web Console, you must do either of the following:
- Obtain a new SSL certificate signed by a trusted Certificate Authority (CA).
- Add the Master Server self-signed SSL certificate to your computer’s list of Trusted Root Certificates.
Obtain Signed SSL Certificate
Obtain a new SSL certificate signed by a trusted CA by generating and submitting a Certificate Signing Request (CSR). This CSR is sent to the CA; the CA uses the details included in the CSR to generate a SSL certificate for the Master Server.
To generate a CSR, run as root on the Master Server console:
openssl req -new -key /var/lib/er2/ui/sslkey.pem -out /var/lib/er2/ui/er2-master.csr
openssl asks for the following information:
| Prompt | Answer |
|---|---|
| Country Name (2 letter code) [AU]: | Your country’s two letter country code (ISO 3166-1 alpha-2). |
| State or Province Name (full name) [Some-State]: | State or province name. |
| Locality Name (e.g., city) []: | City name or name of region. |
| Organization Name (e.g., company) [Internet Widgits Pty Ltd]: | Name of organization. |
| Organizational Unit Name (e.g., section) []: | Name of organizational department. |
| Common Name (e.g. server FQDN or YOUR name) []: | Must be the fully qualified domain name of the Master Server. |
| Email Address []: | Email address of contact person. |
| Please enter the following 'extra' attributes to be sent with your certificate request | - |
| A challenge password []: | Leave empty; do not enter any values. |
| An optional company name []: | Leave empty; do not enter any values. |
- https://er-master/ : Common name is er-master.
- https://er-master.domain.com/ : Common name is er-master.domain.com.
The openssl command generates a CSR file, er2-master.csr. Submit this CSR to your organization’s CA.
To move the CSR file out of the Master Server, see Use SCP to Move the CSR File.
To display and validate the contents of the CSR file, run:
openssl req -in /var/lib/er2/ui/er2-master.csr -text -noout
Use SCP to Move the CSR File
To move the CSR file out of the Master Server and submit it to a CA, use the SCP protocol.
On the Master Server, start the OpenSSH server by running as root:
service sshd start
On Windows
Use a Windows SCP client such as WinSCP to connect to the Master Server via the SCP protocol.
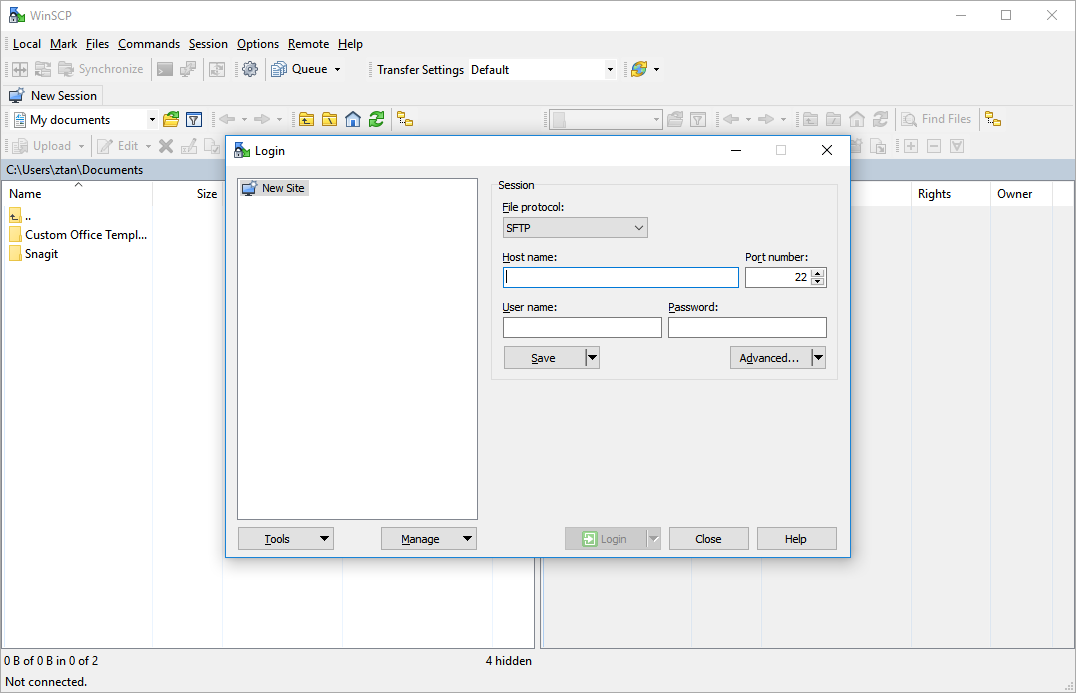
- Start WinSCP.
-
In the Login dialog box, enter the following:
Field Value File protocol Select SCP. Host name Enter the hostname or IP address of the Master Server. Port number Default value is 22. User name Enter root. Password Enter the root password for the Master Server. - Click Save.
- Click Login to connect to the Master Server.
Once connected, locate the CSR file on the Master Server and copy it to your Windows host. Submit the CSR file to your CA.
On Linux
On the Linux host that you want to copy the CSR file to, open the terminal and run:
# Where er-master is the host name or IP address of the Master Server.
scp root@er-master:/var/lib/er2/ui/er2-master.csr ./
This securely copies the CSR file (er2-master.csr) to your current directory. Once the file has been copied, submit the CSR file to your CA.
Add Certificate as Trusted Certificate Authority
The SSL certificate received from the CA must be added to the list of trusted CAs on the Master Server host.
- Copy the SSL certificate obtained from the CA (e.g. ca.cer) to the Master Server. Refer to Use SCP to Move the CSR File for secure copy instructions.
-
On the Master Server, run the command to convert the SSL certificate to .pem format.
# Syntax: openssl x509 -in <input-certificate-file> -outform PEM -out <output-pem-file> openssl x509 -in ca.cer -outform PEM -out sslcert.pem - Copy the SSL certificate sslcert.pem to the /etc/pki/ca-trust/source/anchors directory on the Master Server.
-
Run the following command to update the local trust store on the Master Server:
update-ca-trust
Install the New SSL Certificate
Once you have added the SSL certificate to the list of trusted CAs on the Master Server:
-
Move the SSL certificate sslcert.pem to the /var/lib/er2/ui/ folder on the Master Server.
The source SSL certificate must be a PEM file. If using a different input format, please convert the SSL certificate to .pem format before proceeding. -
(Optional) Display and validate the contents of the PEM file by running:
openssl x509 -in /var/lib/er2/ui/sslcert.pem -text -noout -
Run as root:
chmod 600 /var/lib/er2/ui/sslcert.pem
Restart the Web Console
Restart the Web Console:
-
Find the pid of the ui process by running as root:
ps aux | grep ui # Displays output similar to: # root xxxx 0.1 2.6 427148 13112 ? Ssl 16:22 0:00 /var/lib/er2/plugins/ui -c /var/lib/er2/ui.cfg -pid /var/lib/er2/ui.pid -fg -start # root 1495 0.0 0.1 103312 876 pts/0 S+ 16:22 0:00 grep ui
# The pid of the ui process is xxxx. -
Kill the ui process; run as root:
Running this command incorrectly may cause your system to stop working. Make sure that you run kill -9 on the correct pid.# where the pid of the ui process is xxxx. kill -9 xxxx
Self-Signed Certificates
The Master Server can act as its own CA and issue self-signed SSL certificates.
To issue self-signed certificates, run as root on the Master Server Console:
-
Create a configuration file subjectAltName.conf:
touch subjectAltName.conf -
Open subJectAltName.conf in a text editor, and enter the following information:
[req] default_bits = 2048 prompt = no default_md = sha256 req_extensions = req_ext distinguished_name = dn
[dn] C=SG O=Organization Name CN=www.domain_name.com
[req_ext] basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment subjectAltName = @alt_names
[alt_names] DNS.0=www.domain_name.com
where:- SG is the ISO 3166-1 alpha-2 country code of your current location.
- Organization Name is the name of your organization.
- www.domain_name.com is the domain name with which you access the Master Server. This may be the host name or FQDN of your Master Server.
- Save subjectAltName.conf.
-
Run:
# Generate a new private key. openssl genrsa -out /var/lib/er2/ui/sslkey.pem 2048
# Generates a new Certificate Signing Request `server.csr`. openssl req -new -key /var/lib/er2/ui/sslkey.pem -out /var/lib/er2/ui/server.csr -config subjectAltName.conf
# Generates new SSL certificate. openssl x509 -req -days 365 -in /var/lib/er2/ui/server.csr -signkey /var/lib/er2/ui/sslkey.pem -out /var/lib/er2/ui/sslcert.pem -extensions req_ext -extfile subjectAltName.conf
# Restrict permissions on the generated *.pem files. chmod 600 /var/lib/er2/ui/sslkey.pem
chmod 600 /var/lib/er2/ui/sslcert.pem - Restart the Web Console.
- Add a security exception to your web browser. See Enable HTTPS.