Enterprise Recon 2.13.0
Amazon S3 Buckets
This section covers the following topics:
- Overview
- Licensing
- Requirements
- Get AWS User Security Credentials
- Set Up and Scan an Amazon S3 Target
- Edit Amazon S3 Target Path
Overview
When probing an Amazon S3 Buckets Target, ER2 lists all buckets (if any) in the principal account that the IAM user (whose credentials are used for the scan) belongs to. However, scans can only be completed successfully for buckets that the IAM user has (at minimum) read access to.
Buckets in other principal accounts (cross principal accounts) that the IAM user has (at minimum) read access to can also be probed and scanned. To scan Amazon S3 Buckets in cross principal accounts, add the bucket manually as a new location under the existing Amazon S3 Target.
To add Amazon S3 Buckets as Targets:
To scan specific objects in the Target bucket, see Edit Amazon S3 Target Path.
Licensing
For Sitewide Licenses, all scanned Amazon S3 Targets consume data from the Sitewide License data allowance limit.
For Non-Sitewide Licenses, Amazon S3 Targets require Server & DB Licenses, and consume data from the Server & DB License data allowance limit.
See Target Licenses for more information.
Requirements
| Requirements | Description |
|---|---|
| Proxy Agent |
|
| TCP Allowed Connections | Port 443 |
Encryption
ER2 supports Amazon S3 Buckets that use the following encryption methods:
- Server-side encryption with Amazon S3-managed encryption keys (SSE-S3)
- Server-side encryption with AWS KMS-managed keys (SSE-KMS)
-
Server-side encryption with customer-provided encryption keys (SSE-C)
ER2 supports only one encryption key value for scanning Amazon S3 Buckets protected by SSE-C method. Scan the Target using different credential sets if multiple encryption key values are required to access all objects within a bucket.
Get AWS User Security Credentials
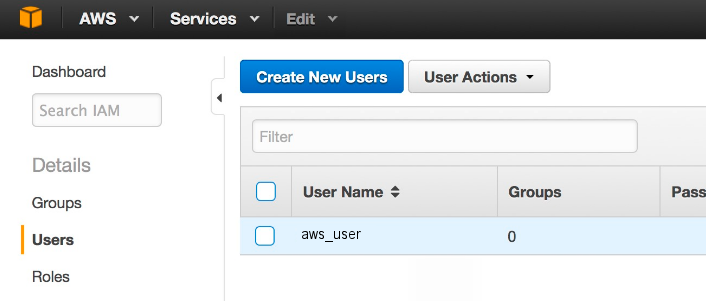
- Log in to the AWS IAM console.
- On the left of the page, click Users and select an IAM user with the
following access permissions to the Amazon S3 Buckets that you want to scan:
- ListAllMyBuckets
- ListBucket
- GetBucketLocation
- GetObject
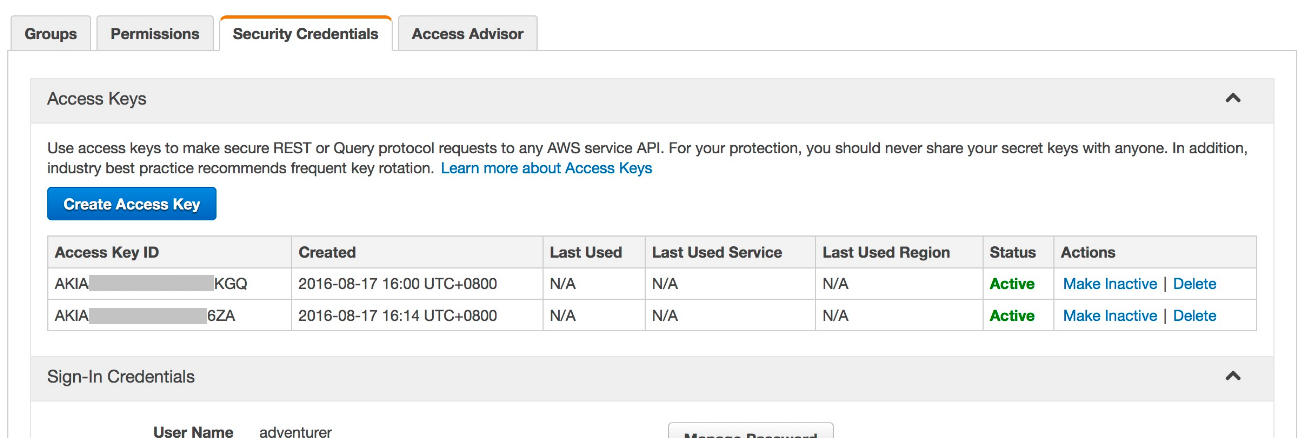
- On the User page, click on the Security Credentials tab. The tab
displays the user’s existing Access Keys.
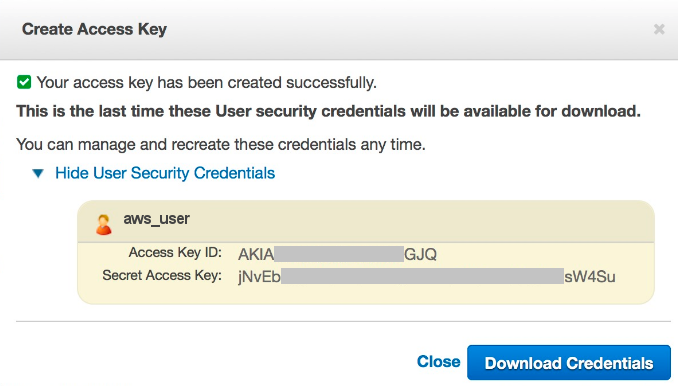
- Click Create Access Key. A dialog box appears, displaying a new set of User security credentials. This consists of an Access Key ID and a Secret Access Key.
- Click Download Credentials to save the User security credentials in a
secure location, or write it down in a safe place. You cannot access this set
of credentials once the dialog box is closed.
Set Up and Scan an Amazon S3 Target
Add Amazon S3 as a Target
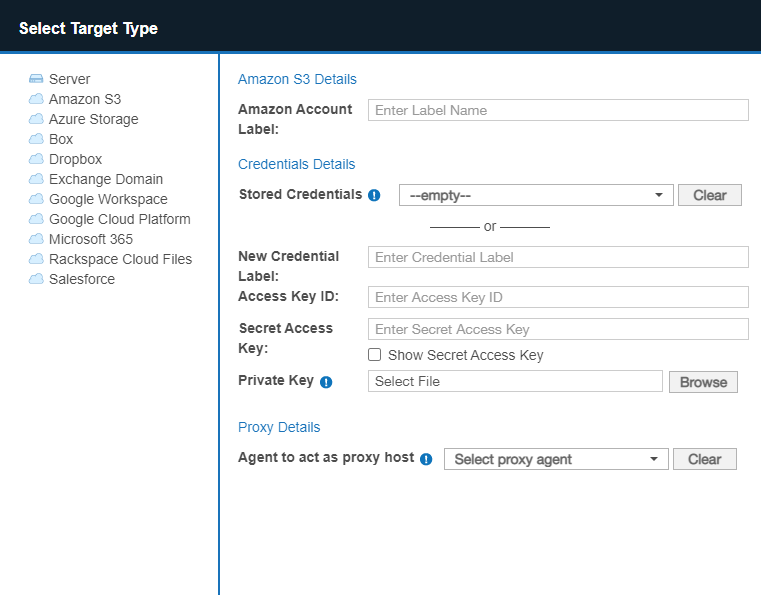
- From the New Scan page, Add Targets.
- In the Select Target Type dialog box, select Amazon S3.
-
In the Amazon S3 Details section, fill in the following fields:
Field Description Label Enter a descriptive label for the Amazon S3 Target.
Example: UserA_Amazon_S3.
New Credential Label Enter a descriptive label for the credential set. Access Key ID Enter the Access Key ID obtained in Get AWS User Security Credentials.
Example: AKIAABCDEFGHIEXAMPLE.
Secret Access Key Enter the Secret Access Key obtained in Get AWS User Security Credentials.
Example: aBcDeFGHiJKLM/A1NOPQR/wxYzdcbAEXAMPLEKEY.
Private Key Upload the file containing the customer-provided 256-bit encryption key.
Only required for Amazon S3 Buckets that use the server-side encryption with customer-provided encryption keys (SSE-C) method for object encryption.
Example: my_amazon_key.txt.
Agent to act as a proxy host Select a Proxy Agent host with direct Internet access. AWS
Please check if your AWS administrator has a set of IAM access keys for your use. AWS advises against using AWS root credentials. Use IAM whenever possible. For more information, see the AWS official documentation.Recommended Least Privilege User ApproachTo reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
- Click Test. If ER2 can connect to the Target, the button changes to a Commit button.
- Click Commit to add the Target.
- Back in the New Scan page, locate the newly added Amazon S3 Target and click on the arrow next to it to display a list of available buckets for the Amazon S3 user.
Scan an Amazon S3 Target
If the credentials used belong to an IAM user in a principal account that does not have buckets, probing the Target will fail. Add the Amazon S3 Target via the Enterprise Recon API instead or upgrade the Master Server to ER 2.10.0.
Scan Buckets in a Single Principal Account
-
In Scans > New Scan page, locate the newly added/existing Amazon S3 Target and select the Target location(s) to scan.
ER2 lists all buckets (if any) in the principal account that the IAM user (whose credentials are used for the scan) belongs to. However, scans can only be completed successfully for buckets that the IAM user has (at minimum) read access to. See Scanning Amazon S3 Buckets in a Single and Cross Principal Accounts for more information.-
If "All data on new target AWSS3:<Amazon_Target_Label>" or "Amazon S3 : All buckets on new target AWSS3:<Amazon_Target_Label>" is selected, ER2 scans all objects contained in all buckets available for the IAM user account.
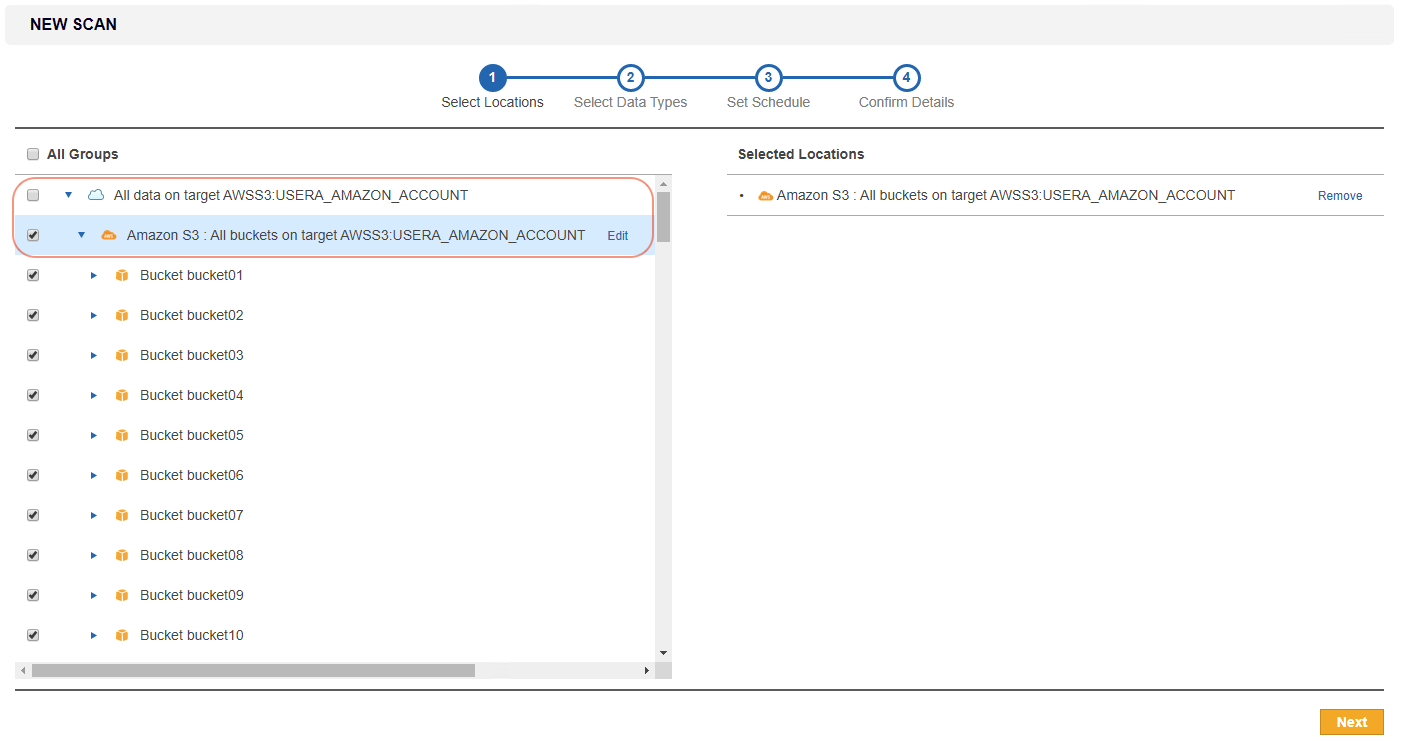 For this setup, ER2 probes and retrieves the buckets under an IAM user account for each instance of a recurring scan. Any new bucket added after the scan was first scheduled is included in the following scan.
For this setup, ER2 probes and retrieves the buckets under an IAM user account for each instance of a recurring scan. Any new bucket added after the scan was first scheduled is included in the following scan. -
If only specific buckets are selected, ER2 scans only the objects contained in the selected buckets.
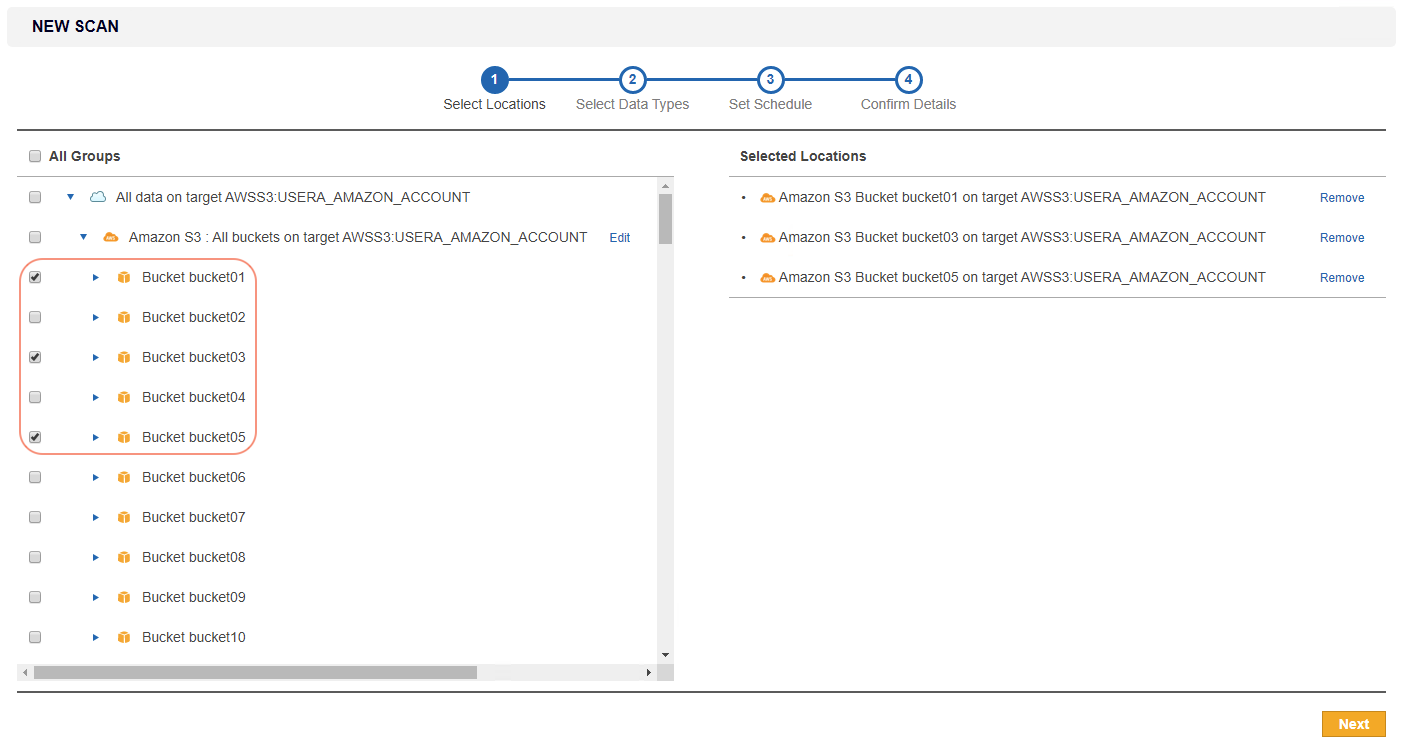 For this setup, ER2 probes and retrieves only the objects in the selected buckets. Any new bucket added after the scan was first scheduled is not included in the following scan.
For this setup, ER2 probes and retrieves only the objects in the selected buckets. Any new bucket added after the scan was first scheduled is not included in the following scan.
-
- Click Next.
- On the Select Data Types page, select the Data Type Profiles to be included in your scan and click Next.
-
On the Set Schedule page, configure the parameters for your scan. See Set Schedule for more information.
- Click Next.
- On the Confirm Details page, review the details of the scan schedule, and click Start Scan to start the scan. Otherwise, click Back to modify the scan schedule settings.
Scan Buckets in Other Principal Accounts
- In Scans > New Scan page, locate the newly added/existing Amazon S3 Target.
- Click Add New Location.
- In the Path field, enter the name of the bucket in the other principal account.
- In the Credentials Details section, fill in the fields using the credentials of the IAM user. See step 3 of Add Amazon S3 as a Target.
-
Click Test and then Commit to save the path to the Target location.
For this setup, ER2 probes and retrieves only the objects in the manually added bucket. Any new bucket added after the scan was first scheduled is not included in the following scan.
Edit Amazon S3 Target Path
To scan a specific object in the Amazon S3 Bucket:
- Add Amazon S3 as a Target.
- In the Select Locations section, select your Amazon S3 Bucket Target location and click Edit.
-
In the Edit Amazon S3 Bucket Location dialog, enter the Path to scan. Use the following syntax:
Path Syntax Whole Bucket <BucketName> Specific folder in Bucket <BucketName/folder_name> Specific file in Bucket <BucketName[/folder_name]/filename.txt> - Click Test and then Commit to save the path to the Target location.