Enterprise Recon 2.0.31
User Permissions
ER2 uses a form of Role-Based Access Control (RBAC) where a user has access to resources and privileges to perform specific tasks based on the roles and permissions granted to the user.
This article covers the following topics:
Overview
A user is granted access to ER2 resources according to the roles and permissions that are explicitly assigned to the user. Permissions can be assigned via:
- Global Permissions: Determines the global settings and resources that a user can manage and access.
- Resource Permissions: Determines the resources that a user can access, and the actions that can be taken on those resources.
- Roles: Contain pre-set combinations of Global Permissions and Resource Permissions that determine the resources that a user can access, and the actions that can be taken on those resources.
Global Permissions
A Global Admin or Permissions Manager can manage the Global Permissions that are assigned to a user.
-
Expand the navigation menu, ENTERPRISE RECON
 .
. - Go to the USERS AND SECURITY > USER ACCOUNTS page.
- Hover over a user, click Edit and navigate to the Roles and Permissions > Global Permissions tab.
Setting Description for <Setting> = On Global Admin Superuser with global administrative rights to manage all resources. User can access and edit all pages on the ER2 Web Console.
The following settings are automatically set to On for a Global Admin:
- System Manager
- Permissions Manager
- Data Type Author
- Allow API Access
System Manager User is granted administrative rights to manage the settings in the following Web Console pages:
- Data Type Profiles
- Network Configuration
- Users and Security
- User Accounts
- Add, edit or delete user accounts
- Security and Compliance
- Access Control List
- User Accounts
- Monitoring and Alerts
- Remediation
Permissions Manager User can manage User Roles and also assign Target and Target Group permissions to user accounts.
See Resource Permissions and Roles for more information.
Data Type Author User can create and share custom data types. Allow API Access User is granted access to the Enterprise Recon 2.0 API. User is only able to access resources to which they have explicit permissions to.
See Permissions Table for a detailed list of components that are accessible for each Global Permissions setting.
Resource Permissions
A Global Admin or Permissions Manager can assign and manage the resources that a user has permissions to. Granular permissions can be assigned for Target Groups, Targets and credentials using the Resource Permissions Manager.
Target Groups and Targets
Target Groups are a means of managing Targets as a group, and for the purposes of permission setting, are treated like an individual Target. Targets must belong to one (and are allowed only one) Target Group.
Credentials
Credentials are credential sets saved by the user to access external resources such as Cloud-based Targets, Database Servers, and Remote Scan Targets. Credential sets are treated as independent objects from the Targets they are related to.
To manage the resources that a user has permissions to:
-
Expand the navigation menu, ENTERPRISE RECON
 .
. - Go to the USERS AND SECURITY > USER ACCOUNTS page.
- Hover over a user, click Edit and navigate to the Roles and Permissions > Resource tab.
- Click on + Add permissions to open the Resource Permissions Manager to add or remove permissions from the user.
Resource Permissions Manager
Target Group
Description
Set user permissions for all or specific Target Groups.
Add multiple Target Groups by pressing the Ctrl key and clicking the selected Target Groups.
Permission Details
- Scan
- User can schedule and manage scans for the selected Target Group.
- Remediate
- Mark Location for Report
- User can only perform remedial actions that mark locations for compliance reports (e.g. Confirmed, Remediated Manually, Test Data, False match, Remove Mark)
- Act Directly on Location
- User can only perform remedial actions that act directly on selected locations (e.g. Mask all sensitive data, Quarantine, Delete Permanently, Encrypt file)
- Mark Location for Report
- Report
- Summary
- User can view or download only high-level summary information about a Target Group.
- User can view the total and breakdown of matches by:
- Match severity (e.g. prohibited data, match data, test data)
- Data type (e.g. American Express, Australian Phone Number)
- Target platform (e.g. Linux 2.6 64 bit, Windows 10 64bit)
- Target type (e.g. MySQL, all local files)
- File format (e.g. XML files, ZIP archives)
- Detailed
- User can view or download detailed information about a Target Group.
- Users can view:
- The total and breakdown of matches by
- Match severity (e.g. prohibited data, match data, test data)
- Data type (e.g. American Express, Australian Phone Number)
- Target platform (e.g. Linux 2.6 64 bit, Windows 10 64bit)
- Target type (e.g. MySQL, all local files)
- File format (e.g. XML files, ZIP archives)
- Details on match locations
- Match data samples and contextual information.
- The total and breakdown of matches by
- Summary
See Reports for more information.
Target
Description
Set user permissions for all or specific Targets.
Add multiple Target by pressing the Ctrl key and clicking the selected Targets.
Access to Targets can be limited to specific paths by defining a Path value. If no Accessible Path is specified, user will be allowed to access all resources on the Target.
See Restrict Accessible Path by Target for more information.
Permission Details
- Scan
- User can schedule and manage scans for the selected Target.
- Remediate
- Mark Location for Report
- User can only perform remedial actions that mark locations for compliance reports (e.g. Confirmed, Remediated Manually, Test Data, False match, Remove Mark)
- Act Directly on Location
- User can only perform remedial actions that act directly on selected locations (e.g. Mask all sensitive data, Quarantine, Delete Permanently, Encrypt file)
- Mark Location for Report
- Report
- Summary
- User can view or download only high-level summary information about a Target.
- User can view the total and breakdown of matches by:
- Match severity (e.g. prohibited data, match data, test data)
- Data type (e.g. American Express, Australian Phone Number)
- Target platform (e.g. Linux 2.6 64 bit, Windows 10 64bit)
- Target type (e.g. MySQL, all local files)
- File format (e.g. XML files, ZIP archives)
- Detailed
- User can view or download detailed information about a Target.
- Users can view:
- The total and breakdown of matches by
- Match severity (e.g. prohibited data, match data, test data)
- Data type (e.g. American Express, Australian Phone Number)
- Target platform (e.g. Linux 2.6 64 bit, Windows 10 64bit)
- Target type (e.g. MySQL, all local files)
- File format (e.g. XML files, ZIP archives)
- Details on match locations
- Match data samples and contextual information.
- The total and breakdown of matches by
- Summary
See Reports for more information.
Credentials
Description
Select the credential sets that will be available to the user.
Permission Details
- Use
- User can use the selected credential set when scheduling scans.
- Edit
- User can modify the selected credential set.
Restrict Accessible Path by Target
Granular permissions can be assigned by defining specific paths that a user can access for a Target.
To restrict user access to a specific path on a Target:
- Open the Resource Permission Manager > Choose Resource and select Targets.
- Click on your selected Target to add it to the right panel.
- Click on + Add path to restrict access to target to add a new path.
- In the dropdown list, select the correct Target type.
- Fill in the Accessible Path value to allow user access only to the specified path.
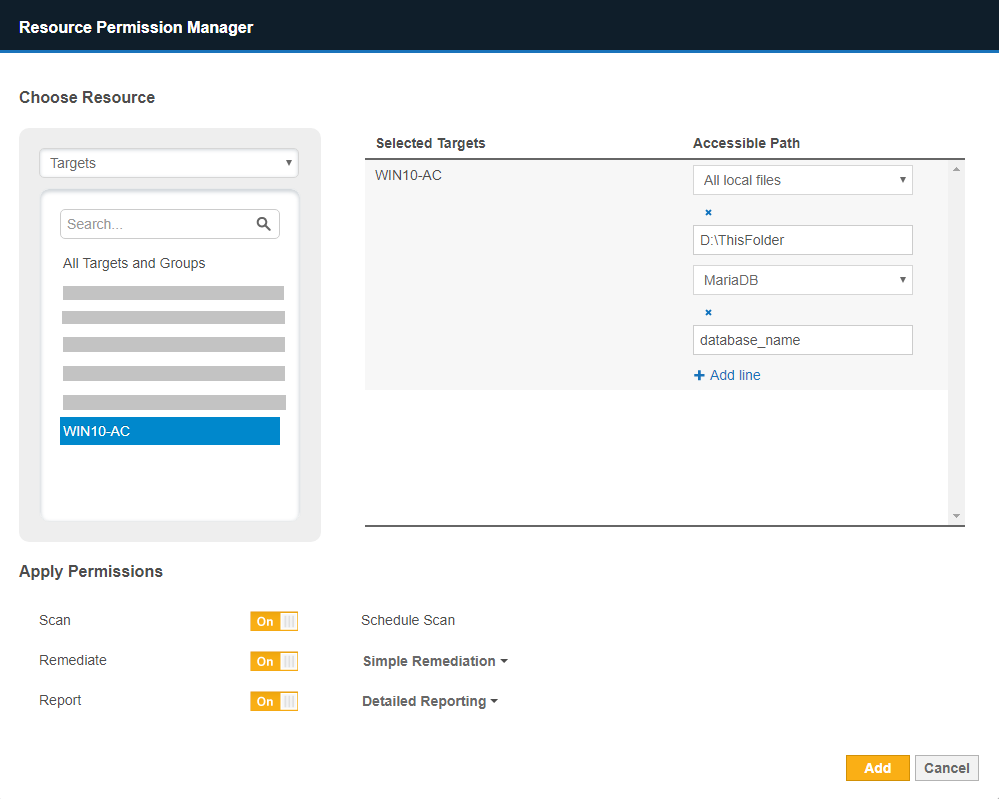
- (Optional) Click on + Add line to add more accessible paths.
- Click Add to save the changes.
Example
Target A is a MySQL database. Credential Set X contains the user name and password to access Target A.
User B is a System Manager who has the following resource permissions:
| Resource | Granted Permissions |
|---|---|
| Target A | Scan, Remediate (Mark Location for Report), Report (Detailed) |
| Credential Set X | Use, Edit |
User B can scan Target A using Credential Set X. User B has the rights to edit Credential Set X when necessary.
If matches are found on Target A, User B can mark these locations for compliance reports but is not allowed to perform any remedial action that acts directly on these match locations.
Permissions Table
Resource permissions and Global Permissions that are assigned to a user grants access to specific components in ER2.
| ER2 Components |
Global Permissions |
Resource Permissions |
|---|---|---|
| DASHBOARD | Target / Target Group: Scan, Report or Remediate | |
| TARGETS | ||
|
Target / Target Group: Scan | |
|
Target / Target Group: Scan, Report or Remediate | |
|
Target / Target Group: Scan | |
|
System Manager and Target / Target Group: Scan, Report or Remediate [1] | |
|
Target / Target Group: Report - Summary Reporting | |
|
Target / Target Group: Report - Detailed Reporting | |
|
Target / Target Group: Remediate - Mark Location for Report | |
|
Target / Target Group: Remediate - Act Directly on Location | |
| SCANNING | ||
| SCHEDULE MANAGER | Target / Target Group: Scan | |
| DATA TYPE PROFILES | ||
|
Data Type Author | Target / Target Group: Scan |
|
Data Type Author | |
|
Data Type Author | |
| TARGET CREDENTIAL MANAGER | ||
|
Target / Target Group: Scan | |
|
Credentials: Edit | |
|
Credentials: Use | |
| GLOBAL FILTER MANAGER | System Manager [2] | Target / Target Group: Scan |
| NETWORK CONFIGURATION | ||
| ACTIVE DIRECTORY MANAGER | System Manager | |
| AGENT MANAGER | System Manager | |
| MAIL SETTINGS | System Manager | |
| NETWORK DISCOVERY | System Manager | |
| USERS AND SECURITY | ||
| USER ACCOUNTS | ||
|
System Manager | |
|
Resource Permissions Manager | |
|
Resource Permissions Manager | |
| MANAGE ROLES | ||
|
Resource Permissions Manager | |
|
Resource Permissions Manager | |
| SECURITY AND COMPLIANCE | System Manager | |
| ACCESS CONTROL LIST | System Manager | |
| MONITORING AND ALERTS | ||
| NOTIFICATIONS AND ALERTS | System Manager [3] | Target / Target Group: Scan [3] |
| ACTIVITY LOG |
System Manager [4] |
Target / Target Group: Scan, Report or Remediate or Credentials: Edit, Use [4] |
| SERVER INFORMATION | System Manager | |
| DOWNLOADS | ||
| NODE AGENT DOWNLOADS | All users. | |
| MY ACCOUNT | ||
| MY ACCOUNT DETAILS | All users. | |
| LICENSE DETAILS | System Manager | |
| API ACCESS | Allow API Access [5] | |
Note:
- [1] System Managers can edit Targets they have visibility to via Scan, Report or Remediation permissions.
- [2] System Managers can import or export Global Filters. System Managers can add Global Filters that apply to all Targets / Target Groups, or add Global Filters that apply only to Targets / Target Groups to which they have visibility to.
- [3] Notification and Alerts are only for Targets and events that the user has permissions to.
- [4] Activity Log only contains events that the user has visibility or permissions to.
- [5] User is able to use the API to access resources to which they have explicit permissions to.
Roles
A Global Admin or Permissions Manager can assign and manage roles that are associated with a user account.
-
Expand the navigation menu, ENTERPRISE RECON
 .
. - Go to the USERS AND SECURITY > USER ACCOUNTS page.
- Hover over a user, click Edit and navigate to the Roles and Permissions tab to see the roles assigned to a user.
- Click on + Add Roles or remove to add or delete roles assigned to the user.
See User Roles for more information.